The Widespread Power of U.S. Law Enforcement to Search Mobile Phones
Logan Koepke, Emma Weil, Urmila Janardan, Tinuola Dada and Harlan Yu
Executive Summary
Every day, law enforcement agencies across the country search thousands of cellphones, typically incident to arrest. To search phones, law enforcement agencies use mobile device forensic tools (MDFTs), a powerful technology that allows police to extract a full copy of data from a cellphone — all emails, texts, photos, location, app data, and more — which can then be programmatically searched. As one expert puts it, with the amount of sensitive information stored on smartphones today, the tools provide a “window into the soul.”
This report documents the widespread adoption of MDFTs by law enforcement in the United States. Based on 110 public records requests to state and local law enforcement agencies across the country, our research documents more than 2,000 agencies that have purchased these tools, in all 50 states and the District of Columbia. We found that state and local law enforcement agencies have performed hundreds of thousands of cellphone extractions since 2015, often without a warrant. To our knowledge, this is the first time that such records have been widely disclosed.
Every American is at risk of having their phone forensically searched by law enforcement.
Law enforcement use these tools to investigate not only cases involving major harm, but also for graffiti, shoplifting, marijuana possession, prostitution, vandalism, car crashes, parole violations, petty theft, public intoxication, and the full gamut of drug-related offenses. Given how routine these searches are today, together with racist policing policies and practices, it’s more than likely that these technologies disparately affect and are used against communities of color.
The emergence of these tools represents a dangerous expansion in law enforcement’s investigatory powers. In 2011, only 35% of Americans owned a smartphone. Today, it’s at least 81% of Americans. Moreover, many Americans — especially people of color and people with lower incomes — rely solely on their cellphones to connect to the internet. For law enforcement, “[m]obile phones remain the most frequently used and most important digital source for investigation.”
We believe that MDFTs are simply too powerful in the hands of law enforcement and should not be used. But recognizing that MDFTs are already in widespread use across the country, we offer a set of preliminary recommendations that we believe can, in the short-term, help reduce the use of MDFTs. These include:
banning the use of consent searches of mobile devices,
abolishing the plain view exception for digital searches,
requiring easy-to-understand audit logs,
enacting robust data deletion and sealing requirements, and
requiring clear public logging of law enforcement use.
Of course, these recommendations are only the first steps in a broader effort to minimize the scope of policing, and to confront and reckon with the role of police in the United States. This report seeks to not only better inform the public regarding law enforcement access to mobile phone data, but also to recenter the conversation on how law enforcement’s use of these tools entrenches police power and exacerbates racial inequities in policing.
Introduction
“We just want to check your phone to see if you were there.”
You know you weren’t at the 7-Eleven — you hadn’t been there in two weeks. You don’t want the cops to search your phone, but you feel immense pressure. “If you don’t give us your consent, we’ll just go to a judge to get a search warrant — do you really want to make us handle this the hard way?” You relent, knowing that they aren’t going to find anything. You quickly sign a form, and the police officers take your phone.
What happens next, in a backroom of the police department, is secretive. Within a few hours, the police have traced almost everywhere you’ve been, looked at all of your text messages, videos, and photos, searched through your Google search history, and have built a highly detailed profile of who you are. This report seeks to illuminate what happens in those police backrooms.
Every day, law enforcement agencies across the country search thousands of cellphones, typically incident to arrest. Often, these searches are done against people’s wills or without meaningful consent. To search phones, law enforcement agencies use mobile device forensic tools (MDFTs), a powerful technology that allows police to extract a full copy of data from a cellphone — all emails, texts, photos, locations, app data, and more — which can then be programmatically searched. By physically connecting a cellphone to a forensic tool, law enforcement can extract, analyze, and present data that’s stored on the phone. As one expert puts it, with the amount of sensitive information stored on smartphones today, MDFTs provide a “window into the soul.”
Law enforcement agencies of all sizes across the United States have already purchased tens of millions of dollars worth of mobile device forensic tools. The mobile device forensic tools that law enforcement use have three key features. First, the tools empower law enforcement to access and extract vast amounts of information from cellphones. Second, the tools organize extracted data in an easily navigable and digestible format for law enforcement to more efficiently analyze and explore the data. Third, the tools help law enforcement circumvent most security features in order to copy data.
Law enforcement agencies of all sizes across the United States have already purchased tens of millions of dollars worth of mobile device forensic tools.
The proliferation and development of mobile device forensic tools in large part mirrors the adoption of smartphones across the United States. In 2011, only 35% of Americans owned a smartphone. Today, it’s at least 81% of Americans. Moreover, many Americans — especially people of color and people with lower incomes — rely solely on their cellphones to connect to the internet. For law enforcement, “[m]obile phones remain the most frequently used and most important digital source for investigation.” In many ways, mobile device forensic tools have helped to vastly expand police power in ways that are rarely apparent to communities.
In 2014, the Supreme Court decided Riley v. California, holding that the warrantless search of a cellphone incident to an arrest was unconstitutional. As a result, today law enforcement need a warrant to search a cellphone. Since this landmark decision, the public debate surrounding evidence on mobile phones has largely focused on the rare cases when law enforcement can’t access the contents of a phone, due to encryption. For example, after the high-profile San Bernardino shooting in 2015 and, more recently, after a deadly shooting at Naval Air Station Pensacola.
However, substantial public attention to these rare, high-profile cases in which law enforcement cannot access the contents of a phone overshadows a more significant change: the rise in law enforcement’s ability to search the thousands of phones that they can access in a wide range of cases, and the power this gives to the police when it has routine and easy access to people’s most sensitive data.
Throughout 2019 and 2020, Upturn filed more than 110 public records requests with state and local law enforcement agencies to determine which agencies have access to mobile device forensic tools, and how they use them. Some have suggested that technologies “to extract data from mobile phones . . . are things that few state and local police departments can afford,” or that this technology is “cost prohibitive, however, for all but a handful of local law enforcement agencies.”
But our research tells a different story. Our records show that at least 2,000 agencies have purchased a range of products and services offered by mobile device forensic tool vendors. Law enforcement agencies in all 50 states and the District of Columbia have these tools. Each of the largest 50 police departments have purchased or have easy access to mobile device forensic tools. Dozens of district attorneys’ and sheriff’s offices have also purchased them. Many have done so through a variety of federal grant programs. Even if a department hasn’t purchased the technology itself, most, if not all, have easy access thanks to partnerships, kiosk programs, and sharing agreements with larger law enforcement agencies, including the FBI.
Despite the widespread proliferation of these tools, there is almost no public accounting of how often or in what kinds of cases law enforcement use these tools. The under-the-radar adoption of these tools also means that there has been little public debate about the risks of these tools and how they shift power to the police.
Law enforcement use mobile device forensic tools as an all-purpose investigative tool for a wide array of cases.
The records we obtained through our public records requests demonstrate that law enforcement use mobile device forensic tools as an all-purpose investigative tool for a wide array of cases. Law enforcement use these tools to investigate not only cases involving major harm, but also for graffiti, shoplifting, marijuana possession, prostitution, vandalism, car crashes, parole violations, petty theft, public intoxication, and the full gamut of drug-related offenses. Few departments have detailed policies governing how and when officers can use this technology. Most either have boilerplate policies that accomplish little, or have no policies in place at all.
This report proceeds as follows. In Section 2, we describe the precise technical capabilities of mobile device forensic tools. With that technical background, in Section 3, we then trace the widespread proliferation of mobile device forensic tools throughout local law enforcement agencies nationwide. Next, in Section 4, we show how agencies routinely use these tools, even for the most mundane cases. In Section 5, we explain the unconstrained nature of these uses, especially as most agencies have no specific policies in place. Finally, we offer policy recommendations for state and local policymakers in Section 6.
This report seeks to not only better inform the public regarding law enforcement access to mobile phone data, but also to recenter the conversation on how law enforcement’s use of these tools entrenches police power and exacerbates racial inequities in policing.
Technical Capabilities of Mobile Device Forensic Tools
We begin with a basic primer on how mobile device forensic tools (MDFTs) work and explain their capabilities with respect to data extraction, data analysis, and security circumvention. Our technical analysis surfaces three key points:
MDFTs are designed to copy all of the data commonly found on a cellphone. Mobile device forensic tools are designed to extract the maximum amount of information possible. This includes data like your contacts, photos, videos, saved passwords, GPS records, phone usage records, and even “deleted” data.
MDFTs make it easy for law enforcement to analyze and search data copied from phones. A range of features help law enforcement quickly sift through gigabytes of data — a task that would otherwise require significantly more labor. This includes mapping where someone has been through GPS data, searching specific keywords, and searching images using image classification tools.
While security features like device encryption have received significant public attention, MDFTs can circumvent most security features in order to copy data. Challenges to access can often be surmounted, because of the wide range of phones with security vulnerabilities or design flaws. Even in instances where full forensic access is difficult due to security features, mobile device forensic tools can often still extract meaningful data from phones.
Our findings suggest that today’s mobile device forensic tools can extract data from most phones and represent a dangerous expansion in law enforcement’s investigatory powers.
MDFTs provide sweeping access to personal information on a phone, enabling “an extent of surveillance that in earlier times would have been prohibitively expensive.” In many circumstances, this access can be disproportionately invasive compared to the scope of evidence being sought and poses an alarming challenge to existing Fourth Amendment protections. Our findings suggest that today’s mobile device forensic tools can extract data from most phones and represent a dangerous expansion in law enforcement’s investigatory powers.
A Primer
Mobile device forensics is typically a two-step process: data extraction, then analysis. MDFTs help law enforcement accomplish both. An MDFT is a computer program and its supplemental equipment (e.g., cables, external storage) that can copy and analyze data from a cellphone or other mobile device. The software can run on a regular desktop computer, or on a dedicated device like a tablet or a “kiosk” computer. These tools are sold by a range of companies, including Cellebrite, Grayshift, MSAB, Magnet Forensics, and AccessData.
The investigator initiates the extraction process by plugging the phone into the computer or tablet. With Cellebrite software (which is similar to other tools), once the tool recognizes the phone, it will prompt the investigator to choose the kind of extraction to be performed, and, sometimes, the categories and time range of data to be extracted, as shown in Figures 2.1 and 2.2. Often, in order to extract data, tools may bypass a phone’s security features by taking advantage of security flaws or built-in diagnostic or development tools.
Figure 2.1
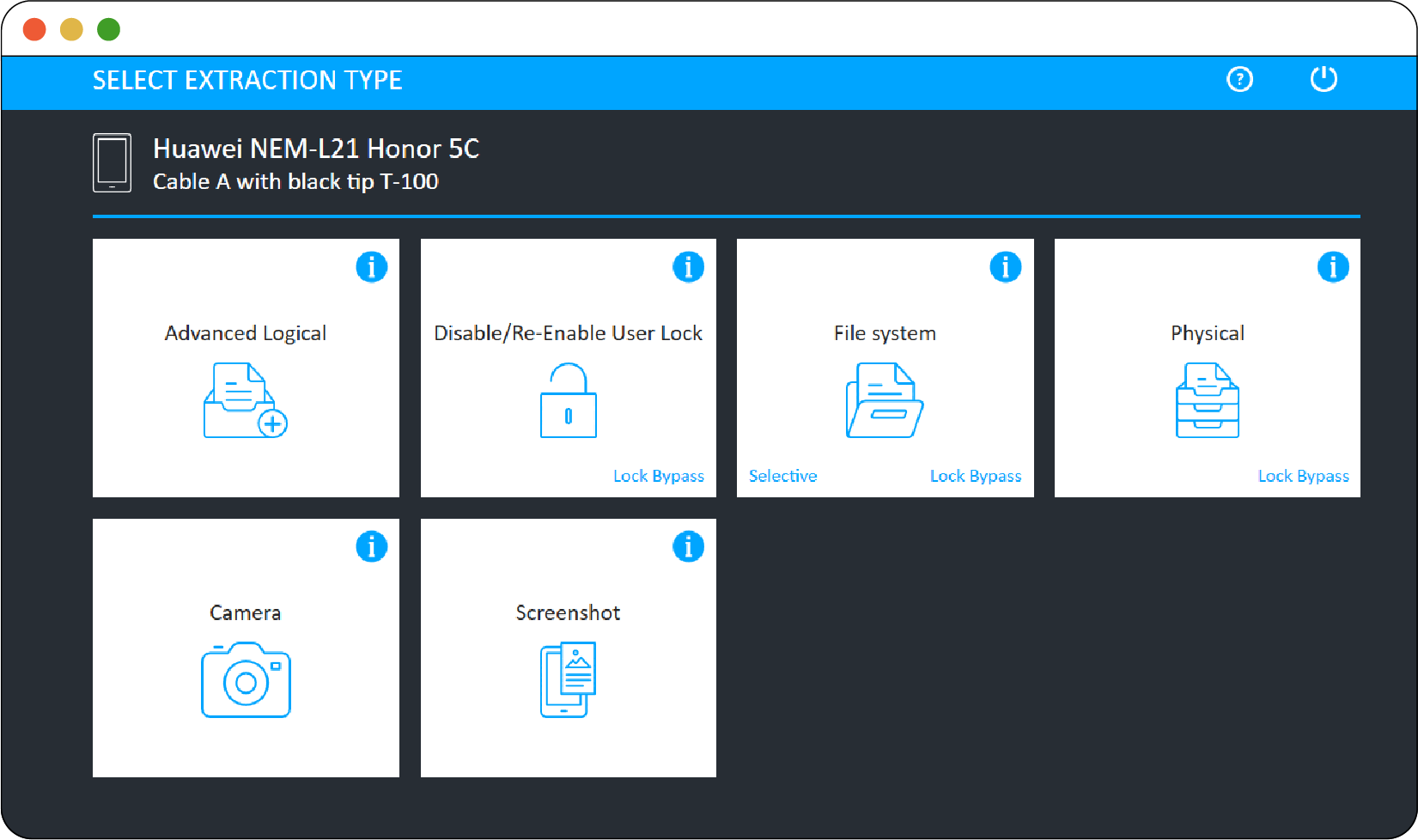
Figure 2.1 shows one of the initial user interface screens of Cellebrite Universal Forensic Extraction Device (UFED). The “Select Extraction Type” screen offers various options for type of extraction and device unlocking.
Figure 2.2
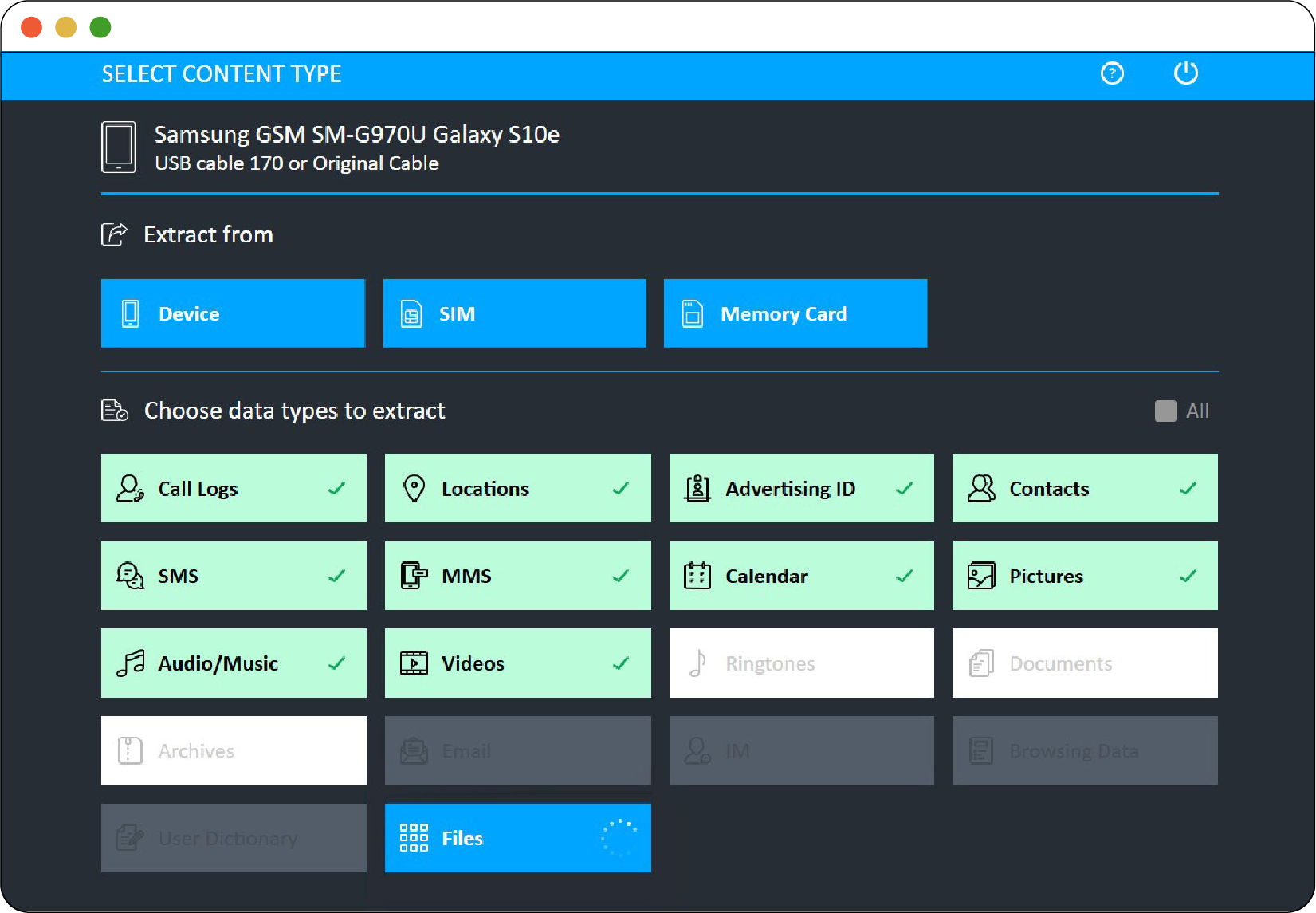
Figure 2.2 shows the “Select Content Type” screen of the Cellebrite UFED user interface, where the user can select the categories of data they want to extract from the phone’s internal storage, SIM card, and/or memory card. There is a convenient option to select “All” categories.
Extraction Methods
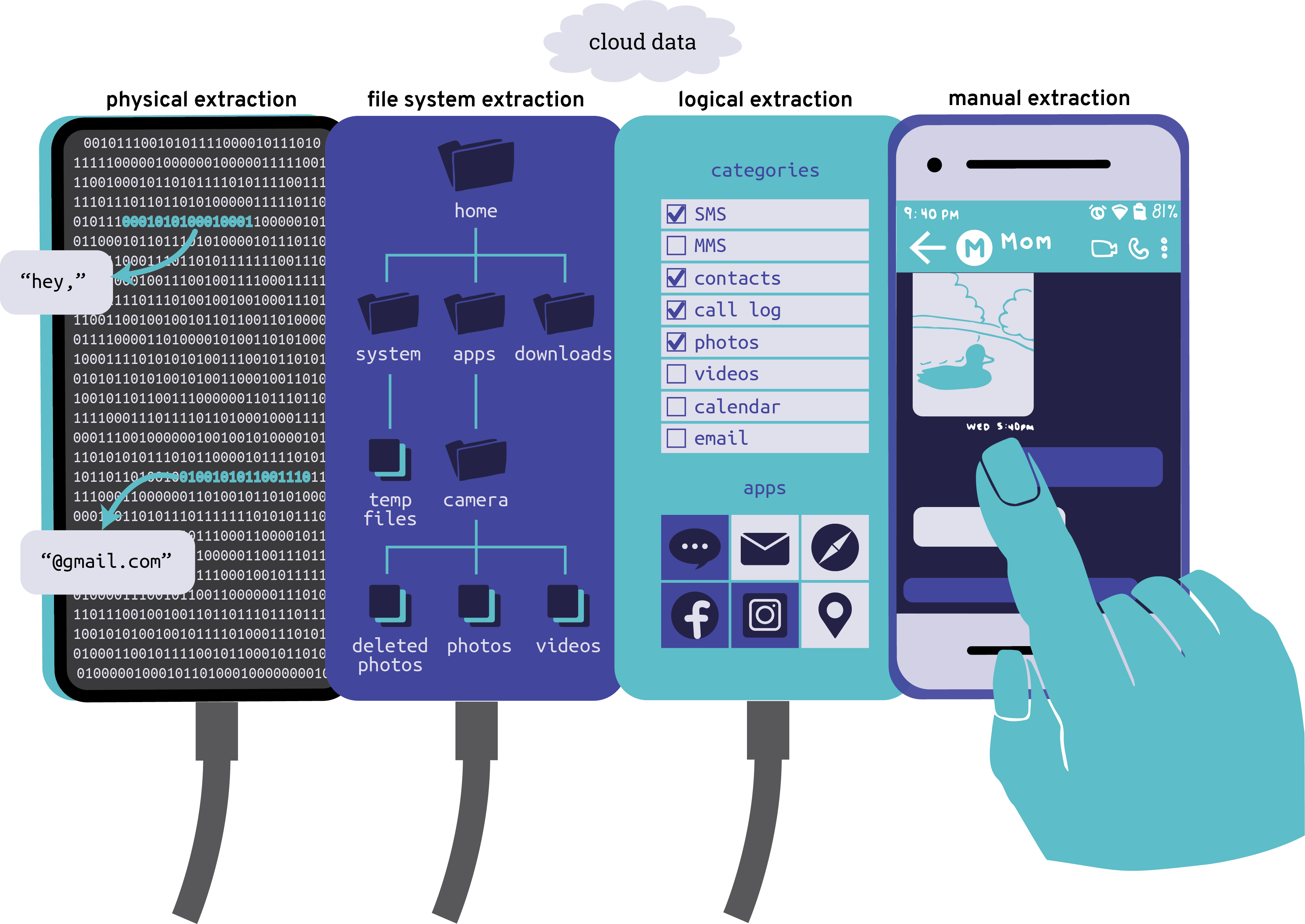
There are a few distinct methods for copying data from phones.
- Manual extraction refers to when an investigator views a phone’s contents like a normal user of the phone. Typically, investigators will take photographs or screenshots of the screen, email data to themselves from the phone, or videotape their exploration of a phone’s contents, to prove that data was actually found on the phone. This process can compromise data integrity, as it may leave new artifacts of use on the phone.
- Logical extraction automates what can be done through manual extraction. In other words, it automatically extracts data that’s presented on the phone to the user, using the device’s application programming interface (API). A logical extraction is like ordering food from a restaurant: what you can get is limited to menu items, and the waitstaff (the API) is in charge of their delivery and organization.
- File system extraction is similar to logical extraction, but it copies even more data — such as files or other data (like internal databases) that a phone doesn’t typically display to users. Continuing the restaurant analogy, this is akin to asking the chef for specific secret dishes outside of the menu, which is possible at some restaurants, but not others.
- Physical extraction copies data as it’s physically stored on the phone’s hardware — in other words, copying data bit-by-bit, instead of as distinct files. This data has to be restructured into files for anyone to make sense of it. A physical extraction is like going to a restaurant and sneaking into the kitchen to take the food directly, as it exists in the kitchen — menu items that are waiting to be brought out, the ingredients used to prepare them, and even what’s in the trash — without mediation from the waitstaff.
In essence, to extract data from a device, some methods work with the phone’s built-in features, while others work around them. Circumventing the phone’s built-in features usually entails more data access, but any extraction method can be invasive because of how much data people store on their phones.
After extraction, law enforcement use MDFTs to efficiently analyze the data — after all, the ability to copy gigabytes of phone data is not worth much if it can’t be effectively searched. For example, law enforcement can sort data by the time and date of its creation, by location, by file or media type, or by source application. They can also search for key terms across the entire phone, just like you might use Google to search the web. This means police can take data extracted from different apps on the phone and view them together as a chronological series of events. It also means they can pull all pictures from the phone to view in one place, regardless of how they are organized on the phone.
Modern cellphones are a convenient combination of many tools: they’re phones, cameras, notebooks, diaries, navigation devices, web browsers, and more. Smartphones centralize patterns of life on a single device with seemingly endless storage. MDFTs allow law enforcement to access all of this data and more, whether or not people knowingly store that information on their phones.
Smartphone photography is a prime illustration of how invasive MDFTs can be. No longer limited by physical prints, people casually accumulate thousands of photos on their phones. In 2017, an estimated 85% of all pictures taken were captured on smartphones, and the number of pictures taken each year worldwide has doubled from 660 billion in 2013 to 1.2 trillion in 2017. MDFTs also extract the embedded metadata from each image file, such as the GPS coordinates of where a photo was taken, and the time and date it was taken. Not only do people carry with them orders of magnitude more photos than they would without a smartphone, but they may also unwittingly carry with them a geographic record of their movements.
MDFTs extract gigabytes of data that are both casually accumulated and unexpectedly revealing. Their core utility is to extract call logs, contacts, text conversations, and photos. However, there is much more stored on phones than these obvious categories. Data from online accounts, third-party apps, “deleted” data, and even people’s precise interactions with the device itself all leave behind artifacts, which MDFTs can find. Through this “gold mine of information,” “the sum of an individual’s private life can be reconstructed.”
Application Data
Virtually every app on a smartphone stores user information, from mobile web browsing history to health tracker data, mobile wallet payments, dating app conversations, and more. MDFTs can copy data for the most popular apps, and are constantly updated to support a wide range of apps. For example, Cellebrite’s tools can extract and interpret data from at least 181 apps on Android’s operating system, and at least 148 apps on Apple iPhones. These apps span from Google apps like Google Maps, Gmail, and Google Photos, to dating apps like Tinder, Grindr, and OkCupid, to Nike+ Run Club, to social media apps like Facebook, Instagram, Twitter, and Snapchat, web browsers like Chrome and Firefox, and even encrypted messenger apps like Signal and Telegram. Because user-installed apps from third parties usually store data in predictable ways, it can be very easy for MDFTs to copy and parse data from them.
MDFTs can copy data for the most popular apps, and are constantly updated to support a wide range of apps.
Account-Based Cloud Data
Not all of the app data on phones are stored on the phone itself. Many apps are account-based, meaning the data in the account is synced to the cloud so that it can be accessed remotely. This means that data created elsewhere on the account may end up existing on the phone, data from the phone may be backed up remotely, and remote data may be viewable from the phone. MDFTs account for each of these possibilities, and many vendors even offer specific features or products to extract cloud backups and other remote account information. For example, Cellebrite offers a UFED Cloud product specifically for these purposes.
One way that MDFTs access account-based information is by copying the account credentials that the phone stores in order to remain logged in, essentially pretending to be the user’s phone. This gives investigators access to any cloud data that the user has access to from their phone, like social media data, emails, or backups of photos and other data. For the most part, this data is not encrypted. For example, an MDFT may be able to pull a remote backup of the phone from Apple’s iCloud service by copying information it finds in the phone’s password management system. And because many services allow users to download all of their data (e.g., Google’s Takeout), MDFTs can access even more sources of data, some of which are shown in Figure 2.3. Figures 2.4 to 2.6 show the process of retrieving account-based cloud data in Magnet’s AXIOM software.
Figure 2.3
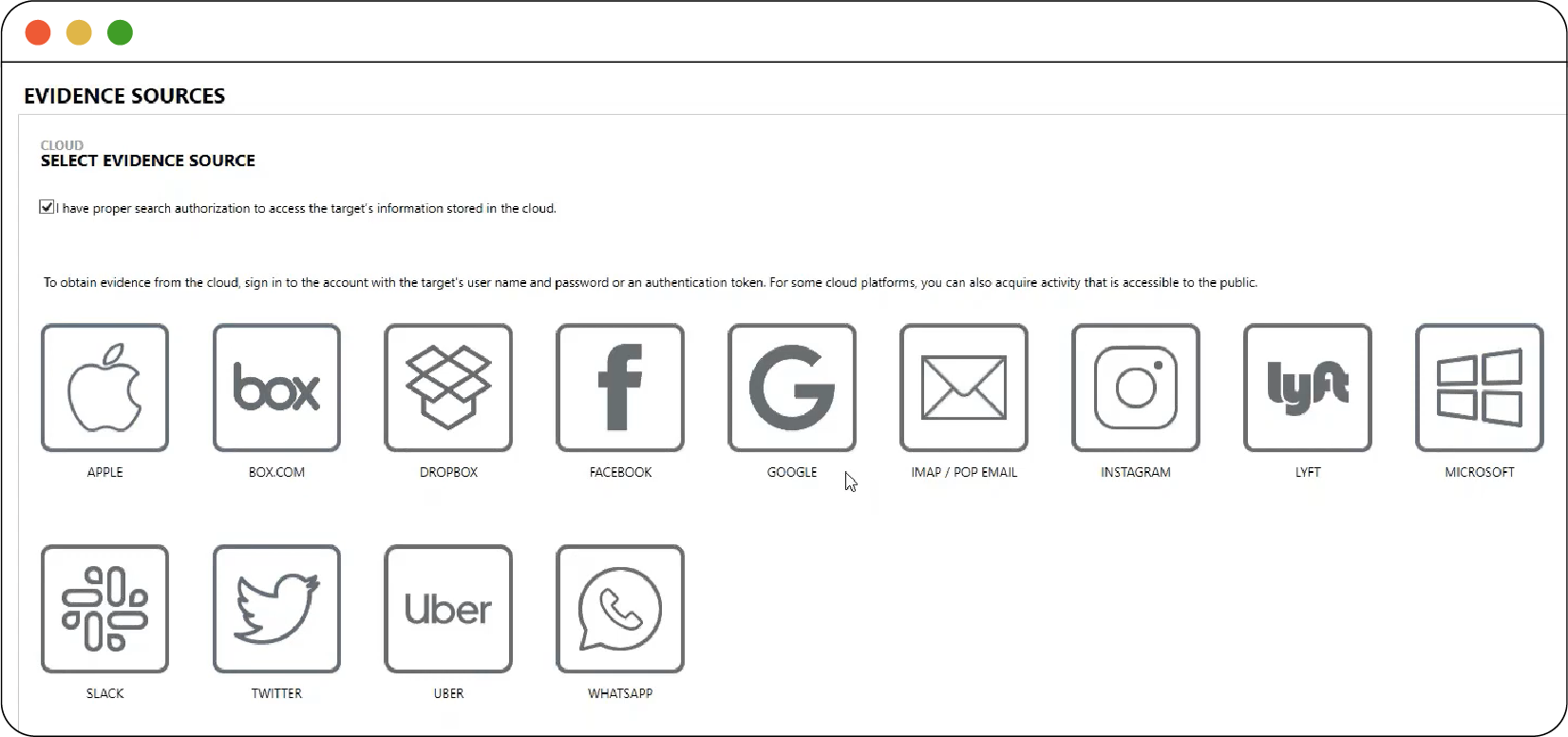
Figure 2.3 shows the user interface of Magnet AXIOM, displaying options to extract remote data from various internet-based accounts.
Figure 2.4

Figure 2.4 shows how Magnet AXIOM allows investigators to use extracted authentication tokens to sign into the device owner’s Microsoft account.
Figure 2.5
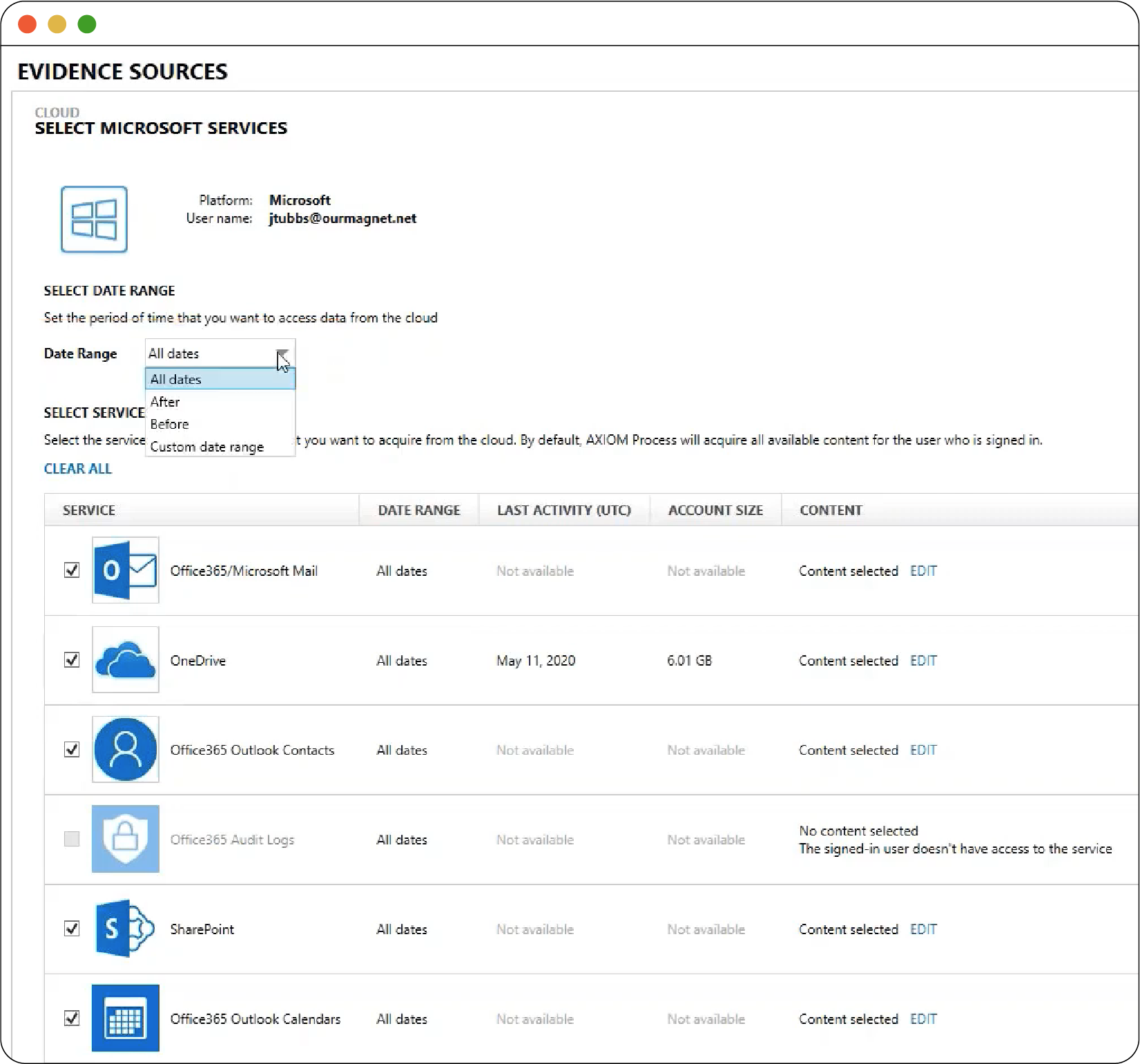
Figure 2.5 shows the Microsoft services thatMagnet AXIOM can extract remotely, like Microsoft OneDrive or Office365.
FIgure 2.6
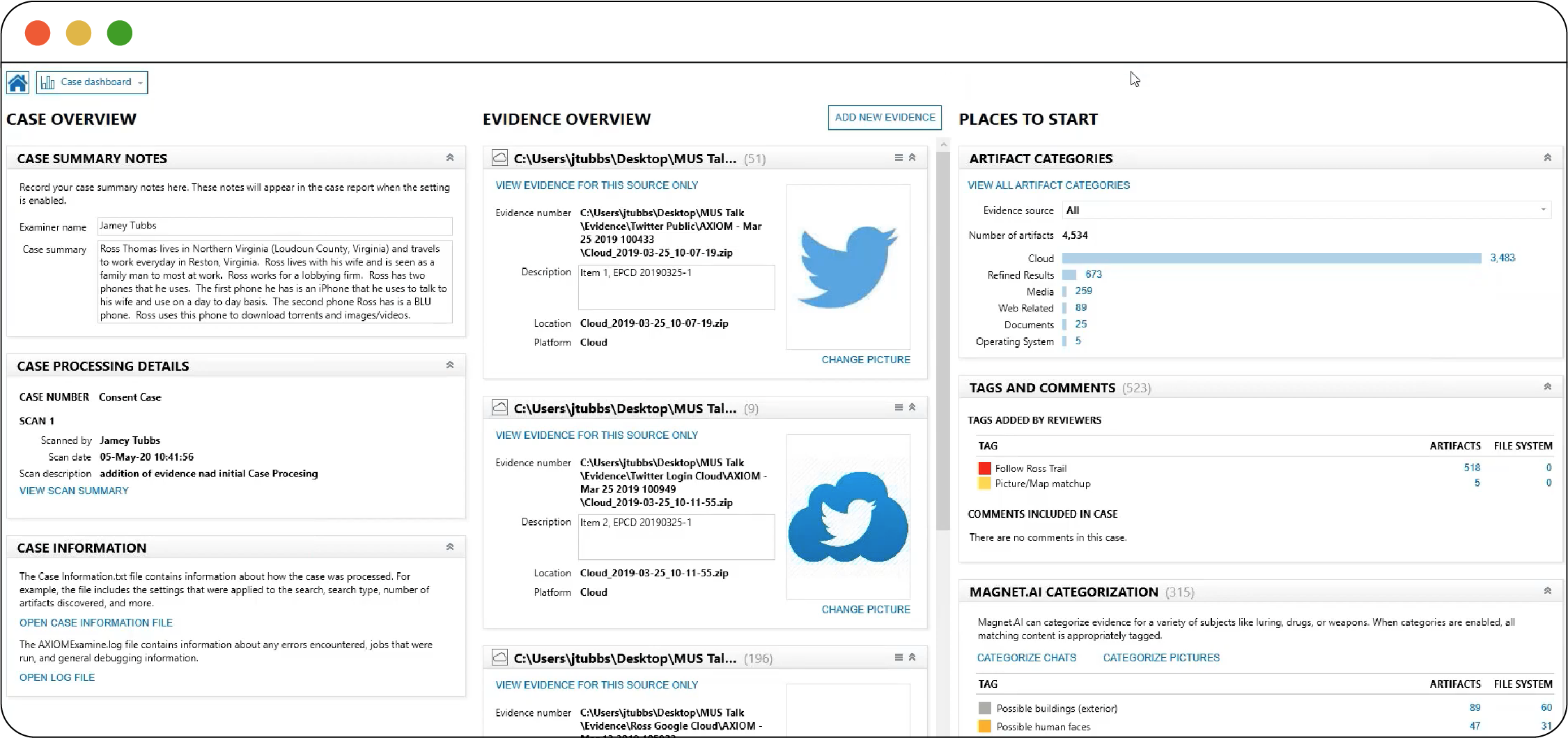
Figure 2.6 shows the dashboard interface of Magnet AXIOM, showing access to Google and Twitter account data, along with other available data called “artifacts.” There are also options to search by image content (“Magnet.AI Categorization”) as well as “Keyword Matches” and “Passwords and Tokens.”
One major source of information is Google’s Location History. Any user with their location history turned on in their Google account will have records of their location stored online in their Google account. These location records are precise and can span years, and many users do not realize this data is being stored. In fact, Google stores this information even when the user is not doing anything that uses the phone’s location. If law enforcement has physical access to a phone, they can use an MDFT to log into the user’s Google account and extract this location history, which can be displayed as a timeline or map, shown in Figure 2.7.
Figure 2.7
Figure 2.7 shows a user’s Google location history as a timeline and also on a map. The timeline can show how long a user stayed at a particular location.
“Deleted” Data
Mobile device forensic tools can sometimes access “deleted” data from phones. Often, deleting a file on a phone isn’t permanent, and the file can be recovered — similar to how most computers have a “recycling bin” for getting rid of files. Deleting a file from the phone itself often doesn’t delete it from a user’s cloud backup, or the variety of other places it may have been redundantly stored at some point. Even “permanently deleted” files can sometimes be recovered with the right tools, because data isn’t always physically wiped from storage when it’s deleted — it’s just marked as “free space” until it’s overwritten by other data. However, access to deleted data depends on a range of factors, including phone hardware, encryption design, and extraction method.
Other Data on a Phone
Phones also record vast amounts of data about how people interact with their devices — data that’s considered a “digital forensics goldmine.” For example, MDFTs can recover logs showing when applications were installed, used, and deleted, as well as how often someone used an application. Other data includes when a device was locked or unlocked, when a message was viewed, when a Bluetooth device was connected, words added to a user’s dictionary, notification contents, as well as past “spotlight searches” on iPhones, a search function that combines on-device and web results. Phones can even store screenshots of apps as they’re brought out of focus so users can see all of the apps they have open. These “behind the scenes” data are stored to improve the phone’s performance, but they leave incredibly detailed artifacts that MDFTs can later analyze.
Ultimately, MDFTs offer law enforcement a powerful window into almost all data stored on — or accessible from — a cellphone, as well as substantial amounts of data that users cannot see. These tools are invasive, especially for people who depend on their phone for internet access because they do not have a computer or broadband.
Data Analysis
Once data is extracted, MDFTs accelerate data analysis with powerful visualization tools. For example, law enforcement can view full text conversations as a chat instead of individual messages in a database; trace a user’s actions on a map or chronological timeline using “patterns of life” metadata; sort data by file type regardless of its location on the phone (e.g., all of the images on the phone, whether they came from the camera app or an email attachment); or create network graphs, like in Figure 2.8, to infer social relationships using contact data.
Figure 2.8
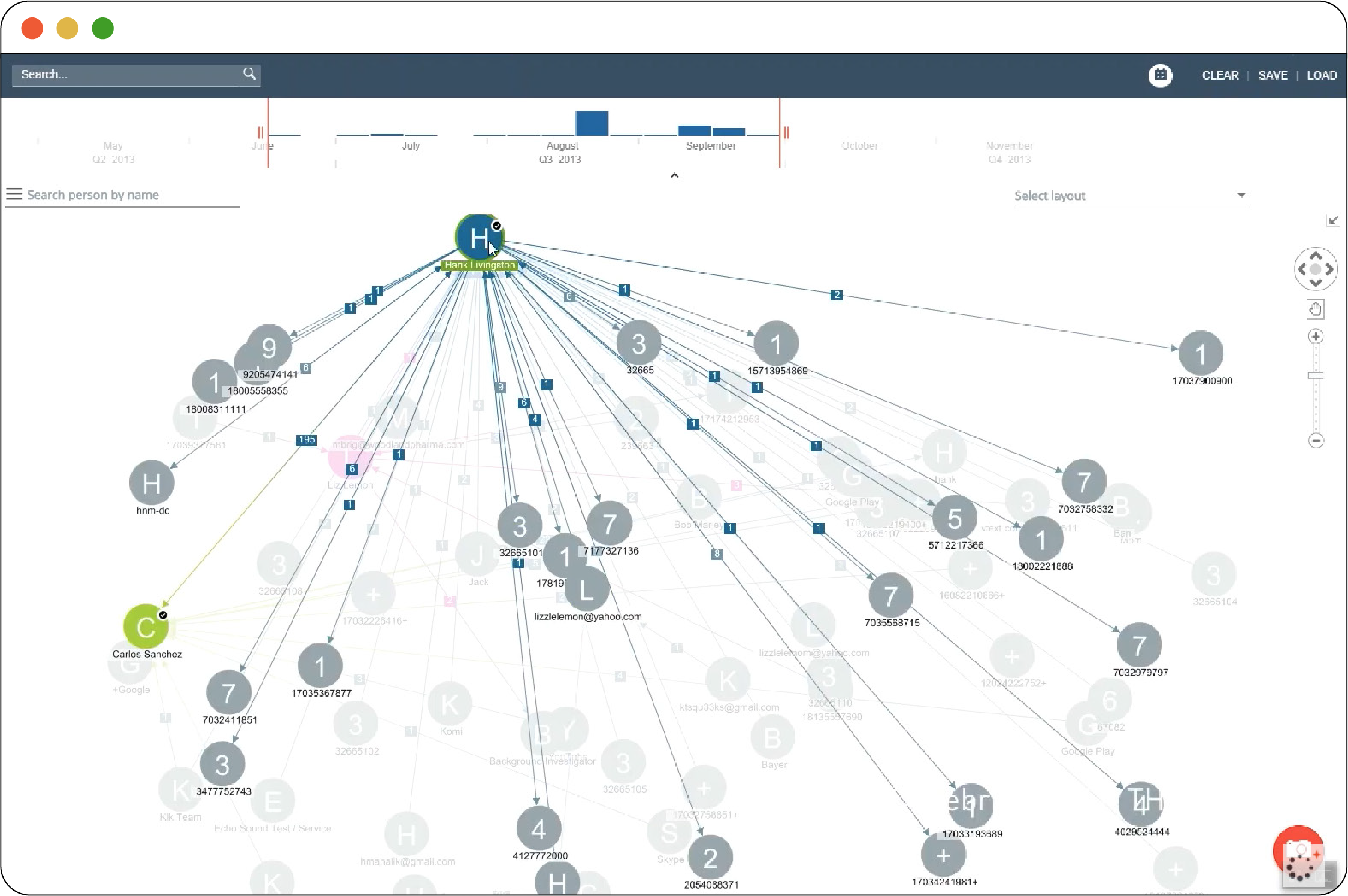
Figure 2.8 shows a screenshot of Cellebrite Analytics, now called Cellebrite Pathfinder, which infers a social graph based on communication events. This graph shows the participants of communications extracted from the phone, as well as a histogram of communication volume over time.
Search features also help law enforcement quickly navigate extracted data. These features include basic keyword searches, as well as more advanced techniques. Some mobile device forensic tools now use machine learning-based text and image classification to categorize file contents, including individual frames in a video. For instance, as shown in Figure 2.9, Cellebrite offers a “search by face” function, whereby law enforcement can compare an image of a face to all other images of faces found on the phone. Cellebrite also allows law enforcement to define new image categories by feeding its software a small set of example images to search for (for example, searching for hotel rooms by giving the software a set of five images of hotel rooms that were taken from Google images). As another example, Magnet Forensics’ AXIOM can employ text classification models in attempts to detect “sexual conversations,” or to filter conversations by topics ranging from family, drugs, money, and police. Tools also allow law enforcement to search for a specific address on a map and view all “location related” events surrounding a point of interest.
Figure 2.9
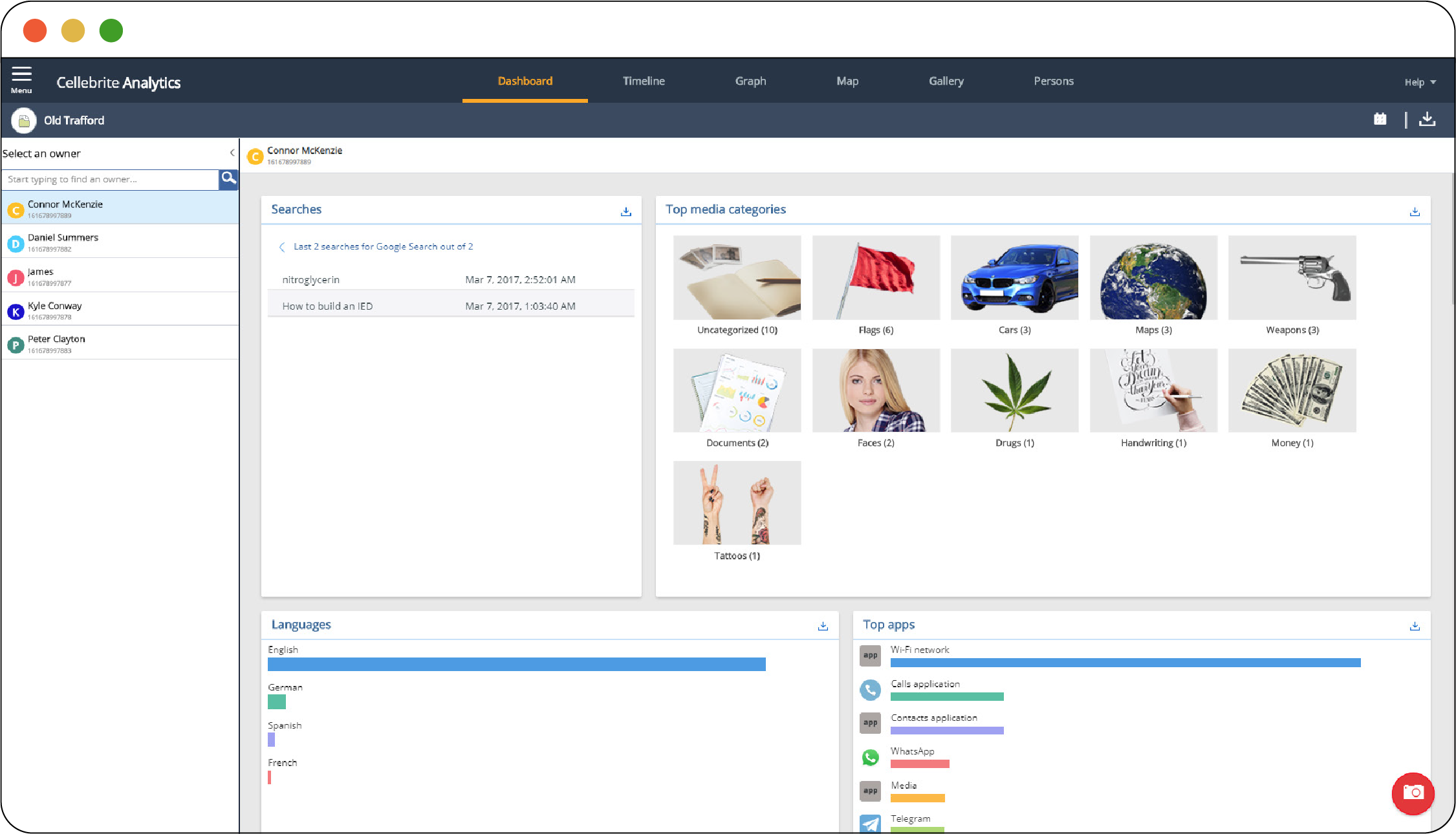
Figure 2.9 shows Cellebrite Pathfinder, which allows investigators to perform an image-based search using pre-generated filters, like “Flags,” “Faces,” “Drugs,” “Weapons,” or “Tattoos.” The software also has features, shown at the top, such as “Timeline” (for viewing events on the phone chronologically), “Graph” (to make a social network graph of contacts and communications), “Map” (to display all phone events and media with location data on a map), “Gallery” (to view all media like photos and videos in one place regardless of source), and “Persons” (to view profiles of discrete users on the phone).
MDFTs can also apply these visualization features to data from multiple phones or other data sources together, to find links across the devices, like common contacts, call or text records, or account information. They can even look for common geolocation or purchase data between phones, to show that the phones were at some point near each other, say, to buy things at the same place and time. What might otherwise take weeks to do manually can be done automatically.
Security Circumvention
Phone manufacturers like Apple, Samsung, Google, and others have built sophisticated security features designed to protect user information in case, for example, a phone is lost or stolen. Manufacturers design these features to balance user convenience with security and privacy. This balancing act can lead to design flaws, software bugs, or other vulnerabilities that law enforcement can then exploit.
MDFTs can often circumvent the security features built into phones in order to extract user data.
MDFTs can often circumvent the security features built into phones in order to extract user data. In response, phone manufacturers continuously patch known security vulnerabilities and develop even more advanced security features, seeking to thwart unwelcome access, including by MDFTs. This “cat-and-mouse game” has evolved over years and continues to this day. MDFTs use numerous tactics to gain access to users’ data on phones, such as guessing a password, exploiting a vulnerability or developer tool, or even installing spyware. With rare exception, MDFTs can nearly always access and extract some, if not all, data from phones.
Many of the phones that law enforcement seize can be extracted with off-the-shelf tools. Departments often purchase tools from multiple vendors to increase the likelihood that any given phone can be extracted. Large MDFT vendors, like Cellebrite and Magnet Forensics, support extraction for thousands of phones. For example, in March 2016, Cellebrite supported logical extractions for 8,393 devices, and physical extractions for 4,254 devices. Since then, out of the five major phone manufacturers, Cellebrite added the most physical extraction support for Samsung (346 devices). Crucially, Cellebrite has also added lock-bypass support (e.g., by exploiting a vulnerability to force the phone to skip the passcode-checking step when it turns on) for about 1,500 devices since March 2016. However, as of 2017, 28% of smartphone users did not even have screen lock enabled on their phones.
MDFT vendors add support for new devices and software at a rapid pace, especially for popular devices. For example, about 45% of U.S. smartphone users have iPhones. iOS 13 was released on September 19, 2019, and Cellebrite announced support for Apple devices running iOS 13 less than three weeks later.
Although iPhones encrypt data by default, there are many phones that still do not support encryption, or have easily surpassed encryption schemes, like lower-end Android phones. Other common targets are phone chipsets or developer tools, which tend to be consistent across brands, meaning a single exploit or method can be successfully reused for a large number of devices. For example, independent researchers recently released the “checkm8” exploit, which takes advantage of a permanent vulnerability in all but the newest iPhone chipsets, providing an opportunity for MDFTs to extract data without knowing the passcode.
MDFTs Can Often Bypass Security Measures
Sometimes, MDFTs cannot immediately extract data from a phone due to encryption and other security features. In those cases, MDFTs often turn to another strategy: repeatedly trying random passwords until guessing the correct one, which then allows the MDFT to decrypt the phone’s contents. MDFTs can also look for unencrypted data on a phone when its password is difficult to guess.
For many phones, the decryption key is generated from the password, so the strength of the protection that encryption provides is directly related to the length and complexity of the user’s password. Shorter or common passcodes are easier to guess. In April 2018, Professor Matthew Green estimated that brute-forcing a passcode on an iPhone would take no more than 13 minutes for a 4-digit passcode, 22 hours for 6 digits, and 92 days for 8 digits. The default length prompted by iOS is 6 digits. For an advanced off-the-shelf tool like GrayKey or Cellebrite Premium, this can mean guessing passcodes in under a day.
However, since the release of the iPhone XS, XR, and XS Max in 2018, which are no longer vulnerable to the major hardware flaw in previous iPhones, the rate of password guessing is much more limited, making them more difficult to access. Nonetheless, the September 2020 Cellebrite Advanced Services information sheet says that they can “determine locks and perform a full file system extraction of all iPhone devices from iPhone 4S to the latest iPhone 11 / 11 Pro / Max running the latest iOS versions up to the latest 13.4.1.”
Separately, without even needing to guess the password, MDFTs can take advantage of the fact that, in order to balance convenience and security, phones don’t actually encrypt all data on a device. Most people still want to receive calls and texts and hear alarms after their phone restarts but before they’ve unlocked it. Accordingly, certain data is unencrypted upon startup, including some account information that is needed to receive notifications. For example, Cellebrite’s UFED Premium claims it can extract data even on locked iPhones. The data that appears “before first unlock” (BFU) even includes parts of Apple’s password manager. Once the iPhone is unlocked after being powered on — “after first unlock” (AFU) — even more unencrypted data becomes available. Vendors like Oxygen Forensics and Grayshift advertise their ability to find and extract these unencrypted data. Figure 2.10 shows all the artifacts exacted from a BFU extraction by Oxygen Forensic Detective. There are thousands of files available, and as one software reviewer highlights: “Yes, all this data is from BFU extraction. Pay attention to the ‘Image Categorization’ – this [is] the new built-in feature . . . that allows [you] to detect, analyze, and categorize images from twelve different categories, such as weapon, drugs, child abuse, extremism and more.”
Figure 2.10
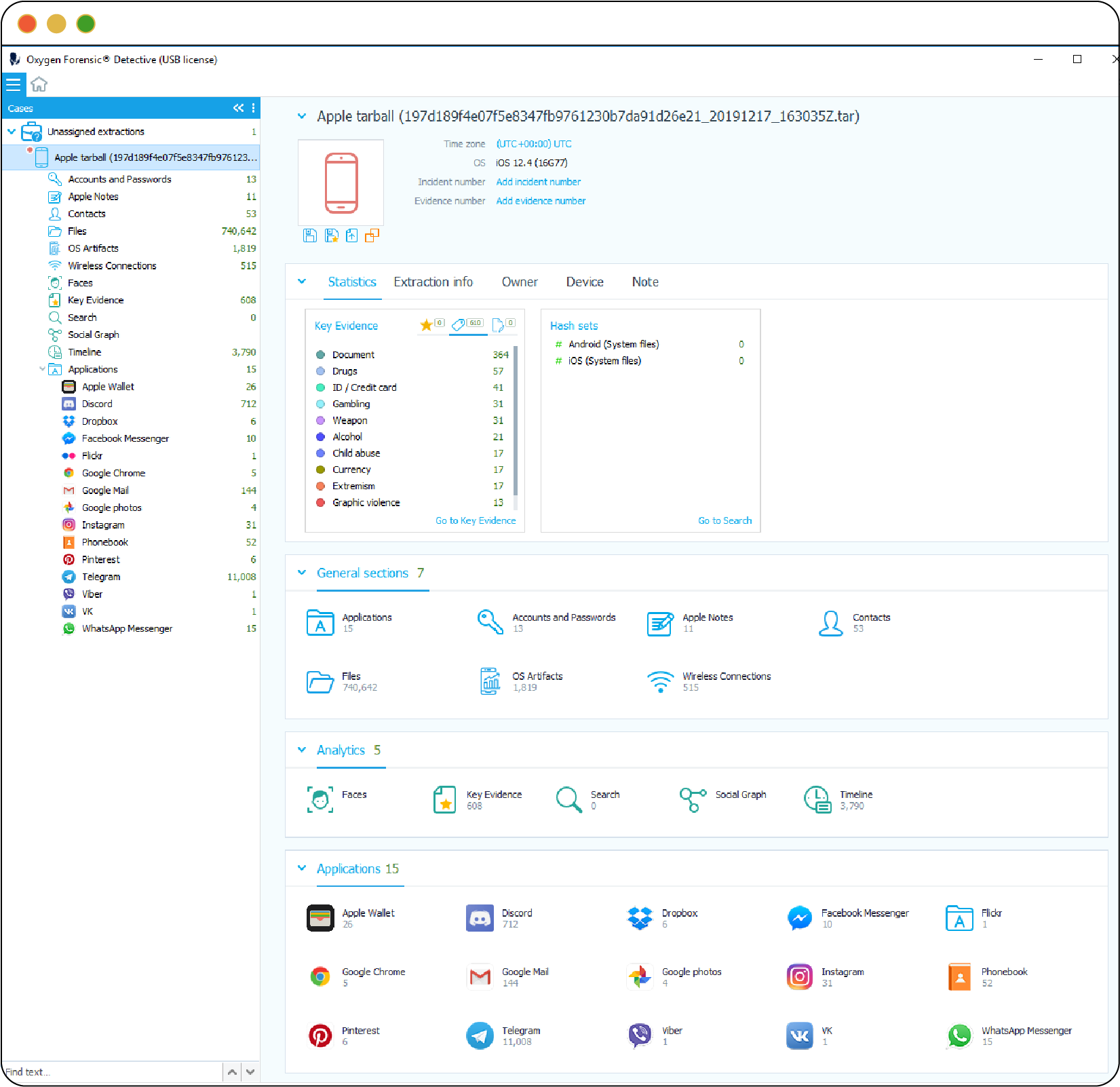
Figure 2.10 shows the result of a “Before First Unlock” extraction by Oxygen Forensics Detective on an Apple iPhone running iOS 12.4. The software detects thousands of files, including 11,000 Telegram files, 712 Discord files, 11 Apple Notes files, 53 Contacts files, 144 files from Google Mail, 26 files from Apple Wallet, and 13 files marked as “Accounts and Passwords.”
When password guessing fails, and BFU or AFU extractions are not workable, MDFTs provide yet other tactics to gain access. For example, Grayshift offers a tool called HideUI, which is essentially spyware that law enforcement installs on a phone in order to record future password entries to eventually access the phone.
Of course, there are even more basic approaches. Law enforcement often seek “consent” to search a person’s phone, but that consent is often not as voluntary as one may assume. People being arrested likely do not understand how much information they are giving away when they consent to a search, even when they presume that information will be exculpatory — yet consent searches happen frequently. We highlight the problems with consent searches in Sections 4 and 6 below.
When All Else Fails, Vendors Offer “Advanced Services”
Although we’ve previously described how the majority of phones can be partially or completely searched, there are some phones that might take specialized effort. For example, one investigator describes being able to get extractions from 25 of 33 (76%) of phones in his cases using just Cellebrite UFED and GrayKey in his lab. To cover the remaining portion of phones, Cellebrite offers “Advanced Services,” which, according to their website, can unlock iOS devices including iPhone 11, 11 Pro/Max, and Android devices including newer Samsung phones.
According to our public records research, the base cost of unlocking and extracting data from a phone using Advanced Services is $1,950, though they can be cheaper in bulk. In 2018, the Seattle PD purchased 20 “actions” for $33,000, and email records show them using Cellebrite to unlock various iPhones within days or weeks. For example, Seattle PD sent Cellebrite an iPhone X with an unknown 6-digit passcode in August 2018: Cellebrite received it on August 24, began processing on August 28, finished processing on September 12, and shipped it back the same day. Today, Cellebrite Premium allows law enforcement to bring these advanced unlocking capabilities in-house for $75,000 to $150,000, based on the frequency of use.
Widespread Law Enforcement Adoption Across the United States
To date, most public reporting on law enforcement use of mobile device forensic tools has focused on law enforcement authorities with the most resources, like the Federal Bureau of Investigation, U.S. Immigration and Customs Enforcement, the Drug Enforcement Administration, and Customs and Border Protection, or on state law enforcement agencies. Much less is publicly known about the availability of these tools to the thousands of local law enforcement agencies across the United States. To find out, we filed more than 110 public records requests to law enforcement agencies across the country, and searched a variety of databases on government spending and grantmaking.
Mobile device forensic tools can cost thousands of dollars for law enforcement agencies. Some have argued that these tools are “cost prohibitive . . . for all but a handful of local law enforcement agencies," or “are things that few state and local police departments can afford." The Manhattan District Attorney’s Office has claimed:
Faced with growing backlogs of encrypted devices, some law enforcement agencies have begun working with private-sector partners to attempt to develop workarounds to obtain contents from otherwise "warrant-proof" Apple and Android phones. This office, with our relatively considerable resources, is one of the few local agencies that can afford to pursue this kind of solution. Other offices lack such resources, which creates an unequal system in which access to justice depends on a particular jurisdiction's financial capacity.
Every American is at risk of having their phone forensically searched by law enforcement.
Our research indicates that this is not the case. Rather, we found widespread adoption of mobile device forensic tools by law enforcement in all fifty states and the District of Columbia. In all, we documented more than 2,000 agencies across the United States that have purchased a range of products and services offered by mobile device forensic tool vendors. Every American is at risk of having their phone forensically searched by law enforcement.
Map 1 shows the proliferation of MDFTs across agencies in the United States. Each dot represents an agency that has purchased at least one MDFT based on our records. We believe many more agencies in the U.S. have purchased MDFTs than the ones we were able to identify.
Almost every kind of law enforcement actor is represented in the data we collected: Local police departments, sheriffs, district attorneys, forensic labs, prisons, housing authorities, public schools, statewide agencies, and more.
Many agencies purchase MDFTs from multiple vendors, including Cellebrite, Magnet Forensics, Grayshift, MSAB, AccessData, and Oxygen Forensics. A single GrayKey unit — which is considered the most advanced iPhone extraction device — costs between $15,000 and $30,000. Cellebrite products vary in cost, but a UFED product costs about $10,000, with a $3,000 to $4,000 annual license fee. The level of spending documented below would allow a law enforcement agency to buy dozens of licenses for different kinds of MDFTs each year, such that they could extract data from numerous phones every day.
MDFT Spending by state
Hover the cursor over a state for more information!
Map 2 shows the total amount of money spent on MDFTs in each state since 2015. Using the toggle alternately shows the amount spent in each state per 100,000 residents, and per 1,000 sworn officers. Total amounts come from our records requests and from our records requests and from financial transparency websites that states offer. Given this, the total amounts shown are likely underestimates.
Almost Every Major Law Enforcement Agency Has These Tools
From documents we’ve obtained, it is clear that the vast majority of large U.S. law enforcement agencies have purchased or used a range of MDFTs. They include:
Every one of the 50 largest local police departments,
State law enforcement agencies in all 50 states,
At least 25 of the 50 largest sheriff’s offices and,
At least 16 out of the 25 largest district or prosecuting attorneys’ offices.
These departments have spent hundreds of thousands of dollars on these tools. For example, the Las Vegas Metropolitan Police Department has spent at least $640,000 on MDFTs, the Miami-Dade Police Department has spent at least $330,000, the San Diego Police Department has spent at least $230,000, the Charlotte-Mecklenburg Police Department has spent at least $160,000, the Tucson Police Department has spent at least $125,000, and the Columbus Police Department has spent at least $114,000. Between 2018 and 2019, the Georgia Bureau of Investigation spent over $610,000 on MDFTs. Since 2018, state agencies in Michigan have spent more than $1.1 million, and the Indiana State Police have spent at least $510,000 on MDFTs since 2015.
Map 3 displays the total amount of money that law enforcement agencies that responded to our public records requests have spent on MDFTs since 2015. Some agency amounts are “unknown” if their response indicated they purchased MDFTs, but did not share with us specific purchase orders or invoices. Appendix C contains the full data underlying this map.
Similarly, sheriff’s offices and district attorneys’ offices have also spent hundreds of thousands on MDFTs: the Broward County (FL) Sheriff’s Office spent at least $560,000, the San Bernardino (CA) Sheriff’s Office has spent at least $270,000, the Santa Clara (CA) District Attorney’s Office has spent at least $250,000, and the Harris County (TX) Sheriff’s Office has spent at least $175,000.
Many Smaller Agencies Can Afford Them
Our research clearly shows that MDFTs are prevalent even among smaller law enforcement agencies.
It may be unsurprising that many of the largest law enforcement agencies in the United States have the resources to acquire these tools. But our research clearly shows that MDFTs are prevalent even among smaller law enforcement agencies. Many are willing to spend a surprisingly large amount of money to acquire these capabilities.
A range of police departments that serve cities of fewer than 100,000 residents have spent tens of thousands of dollars. For example, the Buckeye (AZ) Police Department has spent at least $80,000, the Alpharetta (GA) Police Department has spent at least $66,000, the Bend (OR) Police Department has spent at least $62,000, and the Asheville (NC) Police Department has spent at least $49,000.
Similarly, GovSpend and city data indicate that a range of cities have purchased MDFTs. For example, the City of Shaker Heights (OH) spent at least $136,134, the City of Mansfield (OH) has spent at least $75,000, the City of Superior (WI) has spent at least $61,259, and the City of Walla Walla (WA) has spent at least $59,000. Each of these cities have populations of 25,000 to 50,000. A range of smaller cities, counties, and towns, like the city of Papillion (NE), the town of Whitestown (IN), Jackson Township (NJ), the city of Richland (WA), Glynn County (GA), and the city of Lompoc (CA), have all purchased Grayshift’s GrayKey. Budget documents indicate places like the city of Allen (TX). and the city of Pearland (TX) are planning to purchase GrayKey soon.
These examples underscore how accessible and affordable these tools can be, even for agencies with smaller budgets.
Federal Grants Drive Acquisition
A wide variety of federal grants help law enforcement agencies of all sizes acquire MDFTs. In fact, law enforcement agencies “regar[d] assistance from both federal and state governments as critical to success in digital evidence processing,” especially for smaller agencies, “given [their] more limited potential budgets compared with large agencies." But even larger departments and agencies have estimated that “95 percent of our [mobile device forensic] equipment” comes from outside funding.
Grants from the Edward Byrne Memorial Justice Assistance Grant (JAG) Program have helped a variety of agencies in particular acquire Cellebrite products — such as police in Salt Lake City (UT), Burlington (NC), Sumter (SC), and the Marathon County (WI) Sheriff’s Department. As of this year, the Miami-Dade Police Department is looking to use $283,000 of JAG grant money to buy Cellebrite tools.
The Internet Crimes Against Children (ICAC) task force, a program run by the Department of Justice’s (DOJ) Office of Juvenile Justice and Delinquency Prevention, is a particularly large source of funding for local acquisition of MDFTs. For example, the Arizona Department of Public Safety purchased two GrayKey units with the funds, the Phoenix Police Department used the funds to “complete a project to supply, across the State of Arizona, Cellebrite mobile forensic products," and police departments from Las Vegas, to Dallas, to DeKalb County (GA) used ICAC money to purchase a variety of MDFTs.
Similarly, the DOJ’s Paul Coverdell Forensic Science Improvement Grants Program has provided significant local funding. For example, the Bronx County (NY) District Attorney used the grant money to purchase Cellebrite products. The Charleston (SC) Police Department was funded to purchase two new Cellebrite UFEDs because their digital evidence unit “witnessed a dramatic increase in mobile device submissions." The Alameda County (CA) Sheriff used funds to purchase two GrayKey units, as did forensic science laboratories in Kansas.
Even if a law enforcement agency has not purchased MDFTs themselves, many — if not all — have fairly easy access. One option is to form partnerships with other, larger departments. For example, many larger local law enforcement agencies conduct extractions at the request of smaller nearby agencies. Another option is to turn to state-wide agencies — ranging from the offices of Attorneys General, to state departments of forensics or crime labs — that accept requests to perform examinations of digital devices from local agencies.
Yet another common option is to visit labs run by the Federal Bureau of Investigation (FBI). The FBI maintains 17 Regional Computer Forensic Laboratories with broad capabilities to assist local law enforcement. There are at least 84 locations where “cellphone investigative kiosks” (CPIKs) are available, which allow law enforcement “to extract data from a cellphone, put it into a report, and burn the report to a CD or DVD in as little as 30 minutes.”
From publicly available data, law enforcement used the cellphone investigative kiosks and virtual cellphone investigative kiosks at least 31,000 times between fiscal years 2013 and 2016.
A Pervasive Tool for Even the Most Common Offenses
Our public records requests asked law enforcement agencies for logs of use that identified, among other things, how often and in what kinds of cases law enforcement used MDFTs. The records we’ve obtained can at best tell an incomplete story, as we did not receive records of use from every department we sent records requests to. Only 44 agencies disclosed usage records, and their form varied greatly.
Law enforcement use mobile device forensic tools tens of thousands of times, as an all-purpose investigative tool, for an astonishingly broad array of offenses, often without a warrant. And their use is growing.
But here is the story they do tell: Law enforcement use mobile device forensic tools tens of thousands of times, as an all-purpose investigative tool, for an astonishingly broad array of offenses, often without a warrant. And their use is growing.
These records challenge two prominent, connected narratives surrounding the use of this technology. The first narrative focuses on the rare instances in which law enforcement cannot access the contents of a phone in a high-profile case. The records we obtained document frequent, seemingly routine, everyday instances in which law enforcement do gain access. The second, connected narrative is that these tools are only (or in large part only) used in cases involving serious harm. They are certainly used in those cases — and in some jurisdictions the majority of MDFT use is for cases of serious harm. But such a framing not only misses the dominant uses of these tools, but also completely ignores racially biased policing policies and practices.
Tens of Thousands of Device Extractions Each Year
The records of use we’ve assembled from 44 law enforcement agencies represent at least 50,000 extractions of cellphones between 2015 and 2019. To our knowledge, this is the first time that such records have been widely disclosed.
Importantly, this number represents a severe undercount of the actual number of cellphone extractions performed by state and local law enforcement since 2015 for many reasons. First, this number only captures usage by 44 agencies, while we know that at least 2,000 agencies have these tools, out of more than 18,000 agencies nationwide. Second, some departments that did disclose usage logs did not start tracking their use of MDFTs until recently. Third, many departments that responded indicated that while they possess MDFTs, they do not track or collect how often they use them. Finally, many of the largest local police departments — such as New York City, Chicago, Washington DC, Baltimore, and Boston — have either denied or did not respond to our requests.
Combining all the information we’ve gathered, it’s safe to say that state and local law enforcement agencies collectively have performed hundreds of thousands of cellphone extractions since 2015.
Graffiti, Shoplifting, Drugs, and Other Minor Cases
The records we’ve obtained demonstrate that some law enforcement agencies use MDFTs as an all-purpose investigative tool for a broad array of offenses.
Law enforcement also use these tools to investigate cases involving graffiti, shoplifting, marijuana possession, prostitution, vandalism, car crashes, parole violations, petty theft, public intoxication, and the full gamut of drug-related offenses.
Some law enforcement agencies frequently point to the need to investigate serious offenses like homicide, child exploitation, and sexual violence to justify their use of these tools. And it is certainly true that in some instances, the most common offenses logged in records of use are things like murder or child sexual abuse material — instances where substantial harm has allegedly occurred.
But the records we’ve obtained also tell a different story: that law enforcement also use these tools to investigate cases involving graffiti, shoplifting, marijuana possession, prostitution, vandalism, car crashes, parole violations, petty theft, public intoxication, and the full gamut of drug-related offenses.
Many logged offenses appear to have little to no relationship to a mobile device, nor are the offenses digital in nature. In fact, for many of these alleged offenses, it’s difficult to understand why such an invasive investigative technique would be necessary, other than mere speculation that evidence could be found on the phone.
To better understand law enforcement’s use of these tools, we began seeking out search warrants that law enforcement obtained to search phones. As part of a search warrant, law enforcement submit affidavits — written statements of alleged facts from an agent’s point of view — to a judicial authority. The affidavit must establish probable cause for a search, in this case, of a mobile phone. By examining warrant affidavits, we can begin to understand the routine use of these tools.
These records are imperfect, as search warrant affidavits only provide a law enforcement officer’s perspective on an alleged incident. Nevertheless, these documents can help paint a picture of what allegedly went on prior to law enforcement’s seizure of a phone, and why there is supposedly probable cause to search the phone. A sample of some these incidents include:
After an undercover purchase of $220 worth of marijuana, officers sought to search two phones for evidence of narcotics sales and “other criminal offenses.”
An off-duty officer witnessed what they thought was shoplifting at a Dick’s Sporting Goods Store and said the individuals had left in a Honda Accord. Another officer initiated a vehicle pursuit. Five individuals were arrested and four phones seized. After speaking to the five individuals, officers learned they “had been communicating, via cellphone, throughout the night and were allegedly going to sell the stolen clothing to ‘their regulars.’” Officers sought to search the phones for “plans and correspondence regarding these thefts and the organized crime,” and “[t]he identity of ‘their regulars.’”
Officers witnessed “suspicious behavior” in a Whole Foods grocery store parking lot that they believed to be a “controlled substance exchange” between occupants in a Lexus and a Buick. After the Lexus drove by the unmarked police car, one of the officers “reported the smell the odor [sic] of Marijuana coming through his open window seemingly from the Lexus.” The officers stopped the Lexus because they “did not have a front license plate which is an equipment violation.” Upon searching the car, officers found a small amount of what appeared to be cocaine and marijuana and a black scale. Officers sought to search a subject’s phone for “further evidence of the nature of the suspected controlled substance exchange,” and for evidence “on the knowledge of possession and/or sales of the controlled substances found . . . in [the] vehicle.”
Officers were dispatched to a dispute at a McDonald’s. After arriving, they learned that the dispute appeared to be over $70 that was owed. Apparently, the person who was owed money was “forcing” the person who owed money “to remove his clothing and forcefully removed it as some sort of collateral.” One individual was arrested for charges of simple robbery. Four phones were ultimately seized and officers sought to search them “to further this investigation.”
A plain clothes DEA Task Force Officer was “making consensual contacts” with individuals at the Dallas/Fort Worth International Airport. After asking a traveler “if he had any large sums of US Currency with him,” the officer received consent to search his backpack, and found a large sum of U.S. currency. At this point the subject said he “had used this backpack to store marijuana inside of it before.” Officers then saw a WhatsApp message displayed on the subject’s phone that said “This flower is so good by far one of my fav strands ever.” Officers sought to search the phone for evidence of narcotics sales and money laundering.
A patrol car stopped a vehicle for a “left lane violation.” “Due to nervousness observed and inconsistent stories, a free air sniff was conducted by a . . . K9 with a positive alert to narcotics.” A search of the car revealed several shrink-wrapped bags of suspected marijuana and marijuana wax. Officers seized eight phones from the car’s occupants, and sought to find “evidence of drug transactions, which would provide further evidence with intent to distribute.”
An officer stopped a “white minivan . . . for speeding and traveling in the left lane when prohibited.” The driver was “nervous upon contact.” After denying a consent search of the car, a K9 sniff of the car led to the discovery of marijuana. A search of the car revealed several bags of suspected marijuana. After seizing two phones from the car, officers sought to search the phones for “evidence of drug transactions that will provide further evidence with intent to distribute.”
In a particularly egregious case, officers shot and killed a man after he “ran from the driver’s side of the vehicle” during a traffic stop. Police ultimately discovered a small orange prescription pill container next to the victim. Tests of the pills revealed they were a mix of acetaminophen and fentanyl. After a subsequent search of the victim’s vehicle, officers discovered a phone. Officers sought to search the phone for evidence related to “counterfeit Oxycodone,” “evidence relating to . . . motives for fleeing from the police,” and evidence “relating to the stolen Smith & Wesson SD9 Handgun.”
During an eviction with an “uncooperative” individual, officers shot the individual 15 times after he apparently reached under a blanket for what officers saw as a rifle. Officers seized several cellphones and sought to search them for “any information which would reveal [the individual’s] mindset and motivation at the time of the shooting.”
Officers were looking for a juvenile who allegedly violated the terms of his electronic home monitoring. Officers eventually located the individual and, after a “short foot pursuit . . . he threw several items to the ground,” including a phone. Officers located the phone and sought to search it for evidence of escape in the second degree.
Some departments use MDFTs by and large to investigate drug-related offenses. For example, the vast majority of logged cellphone extractions by the Colorado State Patrol and Baltimore County Police Department are for drug-related offenses. Logs from the Dallas Police Department indicated that drug-related offenses were the second most common offense in which MDFTs were used, behind murder.
For other law enforcement agencies, drug-related offenses are often in the top three or five most common offenses listed in logs we obtained. For example, 20% of phones the Suffolk County (NY) Police Department forensically examined in 2018 were narcotics cases. A log of outside agency cellphone extraction requests to the Santa Clara County (CA) District Attorney’s Office appears to show that drug-related offenses are in the top three most common offenses listed. The same is true of the San Bernardino (CA) Sheriff’s Office. And while drug-related offenses didn’t constitute many cellphone extractions by the Fort Worth Police Department before 2017, they ballooned in 2018 and 2019 to be the third most common offense.
The prominence of drug-related offenses in cellphone extraction logs is especially worrisome given the extreme racial disparities in drug arrests, the disproportionate severity of drug sentences, and the role drug arrests play in deportations. Although none of the extraction logs we received maintained data on race or ethnicity, given this disparity, it’s highly likely that these cellphone extractions disproportionately affect Black and Latinx people.
Almost universally, the search warrants we obtained for drug-related offenses rely on the logic that boils down to a claim that drug dealers use cellphones. An affidavit from a Fort Worth (TX) officer provides a prototypical example:
it is a common practice for individuals involved in the drug trade, to store, keep or conceal contact names, phone numbers, addresses, address books, and contact list of associates, inside cellular telephones, along with logs of incoming and outgoing calls, text messages, e-mails, direct connect data, SIM cards, voice mail messages, logs of accessing and downloading information from the internet, photographs, moving video, audio files, dates, appointments, and other information on personal calendars, Global position system (GPS) data, and telephone memory cards.
For many of the cases in which law enforcement turn to MDFTs, it’s often difficult to assess why such an invasive technique would be necessary at all. Of course, there are some allegations where the connection between the data on a phone and the alleged conduct make it easier for law enforcement to establish probable cause. But there are plenty of cases where the nexus between a phone’s contents and data and the alleged offense is tenuous at best. The use of an MDFT in these cases seems like a drastic investigative overreach.
Officers Often Rely on Consent, Not Warrants
In 2015, the Supreme Court held in Riley that in order to search a cellphone, police must get a warrant. However, “consent searches” have long been understood to be an exception to the Fourth Amendment’s warrant requirement. Our records show that, for some agencies, law enforcement regularly rely on a person’s consent as the legal basis to search cellphones.
For some agencies, law enforcement regularly rely on a person’s consent as the legal basis to search cellphones.
Of the 1,583 cellphone extractions that the Harris County (TX) Sheriff’s Office performed from August 2015 to July 2019, only 47% of phones were extracted subject to a search warrant — the other 53% were consent searches, or searches of phones that were “abandoned/deceased.” Of the 437 cellphones that the Denver Police Department extracted from March 2018 to early April 2019, nearly half were searched pursuant to a search warrant. Approximately one third of the phones the Seattle Police Department sought to extract data from were consent searches.
Of the 497 cellphone extractions that the Anoka County (MN) Sheriff’s Office performed from early 2017 to May 2019, 38% were consent searches of some kind. For the Atlanta Police Department, of the at least 985 cellphone extractions performed from 2017 to early April 2019, about 10% were pursuant to a consent to search form. And for the Broward County (FL) Sheriff’s Office, at least 18% of extractions were based on consent.
Given the broad prevalence of consent searches in other criminal legal contexts, it is perhaps unsurprising that consent searches play a decent role in the searches of mobile phones. We address the problems with consent searches for mobile phones in particular in Section 6.
A Routine and Growing Practice
The records we’ve obtained clearly indicate that law enforcement agencies are using MDFTs for an ever-expanding array of offenses. Given that racial disparities in arrest rates are one of the defining aspects of the American criminal legal system, it’s likely that cellphone extractions already mirror these disparities.
Given that racial disparities in arrest rates are one of the defining aspects of the American criminal legal system, it’s likely that cellphone extractions already mirror these disparities.
In documents we obtained, law enforcement readily admit that these tools are regularly used and internally understood as a standard investigatory tool: “[R]equests for cellphone analysis has become the standard for phones involved in all types of criminal investigation;” “it is used on a daily basis;” “[our department] relies heavily on Cellebrite . . . tools.” In a recent D.C. court opinion, the court noted that “search warrant requests seeking access to cellphone data have become a common feature of law enforcement investigations.”
Statistics on use, where available, help demonstrate that law enforcement use of these tools is growing. For example, the Las Vegas Metropolitan Police Department examined 260% more cellphones in fiscal years 2018-2019 compared to 2015-2016 (from 222 in FY15-16 to 800 in FY18-19). Louisville’s Metropolitan Police Department examined 236% more phones between 2017 and 2018 (from 88 phones to 296). Arizona’s Department of Public Safety use grew 50% from 2015 to 2018 (from 796 phones in 2015 to 1,198 phones in 2018). Honolulu’s Police Department used MDFTs 568% more in 2018 than 2015 (from 25 in 2016 to 167 in 2018). And Dallas’ Police Department noted a 25% increase in cellphone extractions from 2018 to 2019.
Few Constraints and Little Oversight
Despite how invasive MDFTs are, few departments have detailed internal policies that clearly restrict how or when they are used. In our public records requests, we asked each department for any policies or guidelines that would control MDFT use.
Many departments have no policies at all — despite using these tools for years.
Many departments have no policies at all — despite using these tools for years. Nearly half of the departments that responded to our records requests (40 out of 81) indicated they had no policies in place. Even when policies exist, they are often remarkably vague, for instance, by giving general guidance to officers to obtain a search warrant. Among the policies we did receive, we rarely saw any detailed guidance on concerns related to digital searches, such as the scope and particularity of searches, and the retention and use of extracted data. Unsurprisingly, agencies almost always acquire these tools with no public oversight. From our research, we found scant evidence of any community discussion or debate regarding the adoption of these tools.
Many Agencies Have No Specific Policies in Place
Many agencies simply have no policies in place to govern how MDFTs are used. Among the 81 law enforcement agencies that responded to our public records requests, at least 40 of them indicated that they did not have any policies.
Of the 41 policies we received, only nine are detailed enough to provide meaningful guidance to officers. Combined, this means that nearly 90% of the departments that responded to our records requests give their officers wide discretion to use MDFTs and the phone data they collect.
Even very large agencies like the Los Angeles Police Department (LAPD) had no specific policies in place for MDFTs, even though the LAPD has spent hundreds of thousands of dollars on these tools and has used them thousands of times. Other major departments that have no policies include the Houston (TX) Police Department and the Nassau County (NY) Police Department. State law enforcement agencies and county sheriff’s offices are similarly lacking.
Many of the country’s largest and most prominent district attorneys’ offices also use these tools without specific policies, including offices in Manhattan (NY), Cook County (IL), Tarrant County (TX), Philadelphia (PA), Suffolk County (MA), and Dallas County (TX). In their responses to our public records requests, some offices simply noted that they follow applicable case law governing the use of MDFTs. For example, the Manhattan District Attorney’s Office responded that their office “strictly follows and adheres to all applicable federal and state constitutional laws, New York criminal procedure laws, and search and seizure case law in the utilization of this [technology] on a case by case basis.”
The policies we did receive varied substantially in length and detail. Some were nearly 40 pages long; others were barely a paragraph. Some were clearly in the process of being developed; others were boilerplate policies that were too broad to be meaningful. Of course, detailed policies won’t by themselves ensure that people’s rights will be respected. But without them, mobile device searches will expand the power of the police in an even less constrained way. We highlight a few acute problems below.
Overbroad Searches and the Lack of Particularity
The Fourth Amendment to the United States Constitution requires warrants to describe with particularity the places to be searched and the things to be seized.U.S. Const. amend. IV. (“The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”) This “particularity requirement” was designed to protect against “general warrants,” such that law enforcement could not indiscriminately rummage through a person’s property. In addition, the warrant application must identify the specific offense for which law enforcement has established probable cause. To be certain, almost every department policy acknowledges the need to have a sound legal basis to search a phone, whether it’s a search warrant, verbal or written consent, or some other basis, like abandonment or exigent circumstances. But few departments provide much more clarity or direction beyond this general acknowledgement.
Some departments vaguely allude to the need for particularized searches. For example, the Las Vegas Metropolitan Police Department’s Digital Forensics Lab policy notes that “searches that constitute a ‘fishing expedition’ . . . will not be conducted,” but does not add any more detail. Similarly, the Kansas City Police Department’s policy mentions that an examiner “conducting the data extraction will adhere to the details and limitations regarding allowable data extraction and retention as specified in the warrant” — but does not further elaborate on what those limitations can or should be.
In fact, some policies, like the Illinois State Police’s, encourage broad search warrants, noting that “[a]ll computer hardware and software should be included [in search warrant applications], keeping in mind the entire system is necessary to replicate the suspect’s use of it and to enable forensic examination of the system.”
Other policies ask officers to seek broad search authority from the courts, and only to narrow their search when making internal requests to forensic examiners. For example, the Indianapolis Metropolitan Police Department directs officers requesting forensic analysis to describe “the evidence you expect to recover from the exam. Be specific as to what information the examiner should search for, such as ‘Evidence of Dealing Narcotics’ . . . [d]on’t list types of data (e.g. call log, text, email, etc. . . .) as your search warrant should cover all data.” Similarly, the Jacksonville Sheriff’s Office policy notes that failing to provide “details of the investigation and what detailed information the detection seeks from a forensic analysis . . . will greatly increase the processing and analysis time.” In other words, to the extent that law enforcement policies do speak to narrow forensic searches, they do so with reference to productivity and efficiency, not legal authority or constitutional protections.
Relatedly, few policies provide guidance on what examiners should do if they encounter potential evidence of another crime that is not detailed in the initial search warrant. Using a search warrant to look for digital evidence of one potential crime, only to then search for digital evidence of a completely separate crime, raises serious constitutional questions. This practice and limitation is crucial, because without it, law enforcement could go on a “fishing expedition” in search of evidence of any crime, far beyond the original justification for a search. We observed only two policies that provided any guidance on this point.
The risk of overbroad searches is especially worrying given the fact that it’s nearly impossible for those outside of law enforcement — such as a defense lawyer — to repeat the steps that a forensic examiner took and to audit the scope of a search. A handful of agency policies do require examiners to document how a search was conducted, but the level of documentation required is still unlikely to allow a defense lawyer to meaningfully audit a search.
One policy from the Massachusetts State Police states that “[f]ull documentation of all procedures performed and software used should be recorded for every examination and added to the case file.” The Tucson Police Department’s Forensic Electronic Media Unit’s Quality Manual notes that “[n]otes should be taken contemporaneous to the examination or as close as possible.” And the Texas Department of Public Safety’s Computer Information Technology and Electronic Crimes Unit Standard Operating Procedure requires the unit to establish a “peer review process where 20% of all forensic analysis completed will be reviewed,” but they did not provide an example.
There are longstanding legal debates over how to properly govern digital searches: Legal scholars and courts have wrestled with the problems of overbroad digital searches for decades. These arguments are incredibly important, and we surface only some of them in Section 6. Suffice it to say that it’s especially striking, given the prominence of these legal debates, that law enforcement agencies have largely allowed officers and forensic examiners to search mobile phones without detailed policies and with few constraints.
Police Databases and Unrelated Investigations
After law enforcement extracts data from a phone and prepares a forensic report, what happens to the underlying data and how might it be used later? Few policies we received mention any limits on how long extracted data may be retained, or how that data may be used beyond the scope of an immediate investigation.
Absent specific prohibitions, law enforcement could copy data from someone’s phone — say, their contact list — and add that information into a far-reaching police surveillance database. For instance, it’s easy to imagine law enforcement seeing data extracted from mobile phones as providing valuable “leads” for “gang databases,” given the low bar for individuals and their information to be added to such databases. “Gang databases” are notorious, in part, for the loose standards and criteria upon which law enforcement rely to enter people into the databases. Factors can include things like “pictures of the individual displaying perceived gang signals on social media,” “association with known gang members,” “frequenting gang areas,” and other indicators fabricated by law enforcement. This discretion has led to extreme racial disparities in gang databases. Critically, these designations can have profound effects on peoples’ lives: it can “immediately make people ineligible for jobs and housing, subject to increased bail and enhanced charges, and more likely to get deported.” For law enforcement who operate gang databases, data extracted from a phone, like contacts, photos and videos, messages, location history, and more, would be of immediate interest.
Furthermore, forensic analysis tools make it easy for law enforcement to reexamine the contents of a previously extracted phone — it’s as simple as opening a file on a computer. Absent specific policies or laws that require notifying someone that their phone has been searched,For example, the New Mexico Electronic Communications Privacy Act requires notifications to the subject of an investigation contemporaneously with the execution of a warrant. it would be impossible for those under investigation to know of — let alone challenge — situations where law enforcement continues to rifle through previously extracted data for new or unrelated investigations.
There are a small handful of state laws that do prescribe evidence retention periods specifically for digital evidence obtained from cellphones. For example, New Mexico’s recently enacted Electronic Communications Privacy Act requires that “any information obtained through the execution of the warrant that is unrelated to the objective of the warrant be destroyed within thirty days after the information is seized and be not subject to further review, use or disclosure.” However, such laws are far from the norm, and most Americans are currently not protected by these types of data deletion or sealing requirements.
Expanding Searches From a Phone Into the Cloud
Digital forensics practitioners consider cloud data to be “a virtual goldmine of potential evidence.” A recent report from Cellebrite indicated that “one in every two cases requires access to cloud-based data.” As previously discussed in Section 2, major vendors like Cellebrite now sell tools that specifically help law enforcement parlay access to data stored on a phone into further access to data held in the cloud. These tools could, for instance, allow law enforcement to siphon and collect all data from an iCloud account, or all emails from a Gmail account. Or they could allow the police to impersonate the individual. These “cloud analyzer” tools, which are relatively new, represent an immense expansion of law enforcement investigatory powers.
No agency turned over any policies that specifically control the use of cloud data extraction tools.
Yet no agency turned over any policies that specifically control the use of cloud data extraction tools. In theory, unless cloud-based data is specifically detailed in a search warrant for a mobile device, law enforcement should not be able to extract data from the cloud. Cloud extraction poses further challenges: collecting data after execution of a search should require a wiretap order. Search warrants allow for police to get data as of the time of the search warrant’s issuance. But if data keeps coming in, this future collection should be treated like a wiretap.
The National Institute of Standards and Technology’s Guidelines on Mobile Device Forensics advises law enforcement that “[r]etrieval and analysis of cloud based data should follow agency specific guidelines on cloud forensics.” But our research did not find any local agency policy that provided guidance on or control over cloud data extraction.
Rare Public Oversight
The adoption of mobile device forensic tools is almost always a secretive, obscured process. Community engagement on the tools, like other surveillance technologies, is the very rare exception — and in some cases, dissenting voices are deliberately excluded from public discussion. Where it does occur, it is substantially hindered by law enforcement secrecy. Even where existing governance structures ought to facilitate public debate regarding law enforcement use of these tools, these processes are skewed towards law enforcement.
There were a few notable exceptions, but public debate rarely translated into limits on law enforcement use of these tools. For example, the city council of Rochester, New York recently debated an ordinance to allow the Rochester Police Department to purchase a GrayKey. During the city council meeting, the Chief of the Rochester Police Department claimed that the GrayKey would only be “used for solving the most violent crimes we have in Rochester, such as homicide or serious assaults.” In response, one council member asked what the mechanism would be “to ensure that this [technology] is not used for things like a low-level drug offense?” The police chief indicated that “it has to be a certain level of criteria for a judge [to sign off] . . . so it can never be used for a traffic stop, for a marijuana violation.” This claim is, at best, misleading.
Every person who submitted comments to the city council urged the city council to vote no on the Rochester Police Department’s request to purchase GrayKey. One person told the city council that “with the increasing concentration of highly personal information in electronic devices, information not historically available in any form under any type of seizure, tools like GrayKey constitute an unacceptable threat to Fourth Amendment protections.” Another person said that the tool should not be purchased “without explicit policies concerning its implementation, that would include the means to restrict which information is stored, shared, or which information is accessed.” Yet another noted that “devices like this set a precedent for surveillance that more than often directly impacts marginalized communities, specifically black and brown communities.” Ultimately, the city council voted unanimously to authorize the Rochester Police Department to purchase a GrayKey.
Limited community engagement occurred in a handful of other jurisdictions. For example, Davis (CA) and Santa Clara County (CA) both enacted surveillance ordinances that are designed to “ensure residents, through local city councils are empowered to decide if and how surveillance technologies are used.” In both Davis and Santa Clara County, law enforcement had acquired MDFTs before the surveillance ordinances took effect. Nevertheless, the city council and county board of supervisors, respectively, still had to approve surveillance use policies for the tools. In Davis, community members voiced opposition to the use of MDFTs. During an October 2018 public hearing, one commenter noted that “I can only see [this technology] being used to harm marginalized people and to harm people that are fighting [law enforcement] abuse.” Others noted the importance of making statistics on police use of technologies like MDFTs publicly available. Throughout the MDFT surveillance use policy approval process in Santa Clara, there was only one public comment. In both instances, the surveillance use policies were unanimously approved.
Our review of the processes in Davis and Santa Clara indicate that while surveillance ordinances could theoretically play an important role in governing surveillance technologies like MDFTs, their impact has limitations in practice. One reason is that, despite a dedicated process for community oversight, law enforcement agencies were still not forthright with information. For example, the Santa Clara County District Attorney withheld the make and model of its MDFTs from its surveillance use policy to “promote officer safety and maximize the benefits to be derived from the use of data extraction/examination forensic tools and software.” Similarly, the Davis Police Department’s annual surveillance report on its use of Cellebrite UFED provides little helpful information. The report mentions that the tool was “used to serve criminal search warrants on 33 devices for 13 felony investigations,” but provides no more detail. Further, in response to a standard request for “information, including crime statistics, that help the City Council assess whether the surveillance technology has been effective at achieving its identified purposes,” the Davis PD merely responded that “use of the device is still the most effective way to access electronic information on a cellphone.”
Policy Recommendations
We envision a society where systems of policing and incarceration are obsolete. We therefore reject the necessity of both law enforcement and their investigatory tools. Based on our research, we believe that MDFTs are simply too powerful in the hands of law enforcement and should not be used.
We envision a society where systems of policing and incarceration are obsolete.
Below, we offer a set of recommendations that we believe can bring us closer to this vision. Recognizing that MDFTs are already in widespread use across the country, we offer a set of preliminary recommendations that we believe can, in the short-term, help reduce the use of MDFTs. At the margin, further increases in the already formidable tools and data available to law enforcement stand to amplify mass incarceration and worsen racial and other disparities. Therefore, we recommend policy steps that would reduce the tools and data available to law enforcement.
As we considered potential recommendations, we weighed whether or not each would likely reduce the scale of policing, whether it would reduce the tools and data available to law enforcement, and whether it would help challenge narratives that assume law enforcement will increase public safety. We believe that the recommendations we make can limit the power of the police, while not further entrenching the practices that remain. We also recognize that these recommendations are only the first steps in a broader strategy to minimize the scope of policing and reduce the options that police have to bring people into the criminal legal system.
Ban the Use of Consent Searches of Mobile Devices
Police consent searches in any context are troubling, but the power and information asymmetries of cellphone consent searches are egregious and unfixable. Accordingly, policymakers should ban the use of consent searches of cellphones. There are at least three reasons why.
The first reason is that the doctrine underlying “consent searches” is essentially a legal fiction. Courts pretend that “consent searches” are voluntary, when they are effectively coerced. While the Supreme Court has held that the legality of a consent search depends on whether a “reasonable person would understand that he or she is free to refuse,” the so-called “reasonable person” standard fails to account for the important racial differences in how individuals interact with law enforcement. As one scholar noted, “many African Americans, and undoubtedly other people of color, know that refusing to accede to the authority of the police, and even seemingly polite requests—can have deadly consequences.” While the Supreme Court has held that consent cannot be “coerced, by explicit or implicit means,” the notion that someone can actually feel free to walk away from an interaction with police has an “air of unreality” about it. Given the extreme power asymmetries, it’s a “simple truism that many people, if not most, will always feel coerced by police ‘requests’ to search.”
A recent study designed “specifically to examine the psychology of consent searches” highlights the problems in relying on a so-called “reasonable person” to adjudicate consent searches. Participants were brought into a lab and presented with “a highly invasive request: to allow an experimenter unsupervised access to their unlocked smartphone.” More than 97% of participants handed over their phone to be searched when requested to, even though only 14.1% of a separate group of observers said that a reasonable person would hand over their phone. The study reveals that there is a “systematic bias whereby neutral third parties view consent as more voluntary, and refusal easier, than actors experience it to be.” While there are plausible arguments that the lab-setting studies overestimate compliance rates in police searches, there are stronger arguments that they actually underestimate them.
Second, someone consenting to a search of their phone likely doesn't even have a rough idea of what’s really about to happen to their phone. The Fifth Circuit Court of Appeals recently held that a reasonable owner of a cellphone would functionally understand that a “complete” cellphone search “refers not just to a physical examination of the phone, but further contemplates an inspection of the phone’s ‘complete’ content.” But, given the lack of public discussion of MDFTs, many people would likely be surprised by the power of the tools that law enforcement use to extract and analyze data from a phone. Further, most of the consent to search forms we obtained from law enforcement agencies don’t clearly specify how they will search the phone, the tools they’ll use, or the extent of the search.
Finally, law enforcement can do almost anything with data extracted from a cellphone after someone consents. At least one case appears to suggest that, so long as a consent form is written broadly enough, there’s no limit on when law enforcement could re-examine a cellphone extraction. The consent form at issue in that case and the consent forms we obtained are strikingly similar. One form from the Indianapolis Metropolitan Police Department says that “said search may take an extended period of time, however this time normally does not exceed sixty (60) days from the time of consent.” The U.S. Border Patrol claims they can store data extracted from phones searched at the border for 75 years.
Banning consent searches is not a new suggestion. Nor is it a perfect solution, as it’s easy for law enforcement to obtain a search warrant. But banning consent searches of cellphones can help limit police discretion, limit the coercive power of police, and minimize the amount of information that can be collected from people under investigation. State and local policymakers should ban consent searches of cellphones.
Abolish The Plain View Exception for Digital Searches
The plain view exception for digital searches should be eliminated. In a digital search, forensic analysis software can far too easily expose data unrelated to the immediate search, unrestricted by where the data physically resides on the phone. The idea that digital evidence can exist “in plain view” in the way that physical evidence can, when considering how software can display and sort over-seized data, is incoherent.
For physical searches, the plain view exception to the warrant standard allows law enforcement to seize evidence in plain view of any place they are lawfully permitted to be, if the incriminating character of the evidence is immediately apparent. For example, if law enforcement were lawfully searching a house for stolen credit cards, but came across cocaine on the kitchen counter, the plain view exception would allow law enforcement to seize the drugs. In other words, if law enforcement are authorized to search for one thing, but come across another thing that’s clearly incriminating, the plain view exception allows them to seize that thing.
This exception may have made sense in the physical world, but it collapses in the digital world. When law enforcement extract all of the data from a cellphone, and then perform a search across all of that data, everything comes into “plain view.” Traditionally, the plain view exception is limited by a range of physical factors, such as the size and opacity of closed containers. Only so much can become visible, lawfully, during a search of a physical environment, like the home.
Each of these limitations is upset by the digital environment. In digital searches, “[n]early everything can come into plain view and be subject to use in unrelated cases. The result seems perilously like the regime of general warrants that the Fourth Amendment was enacted to stop.” Because forensic software continues to provide law enforcement with ever more powerful search capabilities, the notion of data being “in plain view” is without limit. A search for one kind of digital evidence will almost inevitably reveal troves of other digital evidence. Searching for certain data or keywords, organizing data chronologically, or clicking on different types of extracted data fundamentally changes what’s in “plain view” for the investigator.
The Supreme Court has held that the plain view exception “may not be used to extend a general exploratory search from one object to another until something incriminating at last emerges.” The trouble is, “[c]urrent law allows computer searches for evidence to look disturbingly like searches for all evidence.”
The basic equation for digital searches of cellphones is this: technologies like MDFTs empower law enforcement to seize everything and see everything, and the plain view exception effectively allows law enforcement to do anything during those searches.
As it stands today, the basic equation for digital searches of cellphones is this: technologies like MDFTs empower law enforcement to seize everything and see everything, and the plain view exception effectively allows law enforcement to do anything during those searches. The result: protections guaranteed by the Fourth Amendment are made meaningless. The response from courts across the United States has been tepid, at best. Intervention is necessary.
It’s worth considering the counterarguments. One frequent argument in support of the plain view exception for digital searches is that investigators cannot be restricted in their search because potential suspects can and will conceal evidence within a computer’s storage. As the argument goes, suspects may obfuscate the location of information by storing data in unanticipated places, with random file names and paths to mislead an investigator. As a result, digital evidence can exist anywhere on a device and investigators need the legal tools to find it.
While someone can fairly easily change where data is stored on a computer, it’s significantly more difficult — and in many instances, technically impossible — on cellphones. A cellphone’s user interface is significantly more limiting than a desktop computer’s, often restricting the ways that users can manipulate files. On a desktop, it’s easy to move files around, change file names, or save files into folders or subfolders. Such capabilities are far more limited on a mobile device. Nevertheless, MDFTs allow police to search all of the data on the phone, as if most users have the technical expertise to hide data in arbitrary locations on their phone. With cellphones in particular, the argument that evidence could be hidden anywhere rings hollow.
Abolition of the plain view exception could take several forms. Congress could pass a law to bar the plain view exception for digital searches by amending Rule 41 of the Federal Rules of Criminal Procedure. State legislatures in states that have criminal procedure rules could take similar action. And judges could require, as a condition of issuing a search warrant, that law enforcement agents forswear reliance upon the plain view exception.
The Supreme Court has held that “a cellphone search would typically expose to the government far more than the most exhaustive search of a house.” As a result, it’s time to address the existing loopholes in Fourth Amendment doctrine.
Require Easy-to-Understand Audit Logs
State and local policymakers should require that mobile device forensic tools used by law enforcement have clear recordkeeping functions, specifically, detailed audit logs and automatic screen recording. This would incentivize MDFT vendors to build this functionality. With such logs, judges and others could better understand the precise steps that law enforcement took when extracting and examining a phone, and public defenders would be better equipped to challenge those steps. Audit logs and screen recordings would document a chronological record of all interactions that law enforcement had with the software, such as how they browsed through the data, any search queries they used, and what data they could have seen.
There is an extreme power and resource imbalance between public defenders and law enforcement. This disparity is only exacerbated by defenders’ technological and resource disadvantage: Few public defenders have access to MDFTs. Instead, defenders are often forced to examine forensic reports that are thousands of pages long and “easily navigable only if you have a forensic company’s proprietary software.” Further, defenders and judges often have no way of knowing whether law enforcement actually stayed within the bounds of a search warrant for a phone. For courts, simply taking law enforcement’s word for it should be insufficient — lying under oath is endemic to the institution of American policing. Audit logs would be especially helpful for defenders trying to suppress evidence that was obtained in a prohibited manner.
This recommendation even comports with principles articulated by law enforcement associations, like the Association of Chief Police Officers, which has said that “[a]n audit trail . . . of all processes applied to digital evidence should be created and preserved. An independent third party should be able to examine those processes and achieve the same result.”
Critically, audit logging is unlikely to be an effective tool for broad transparency and police accountability. This tool will not improve police behavior. But on a case-by-case basis, this tool could give public defenders and judges a significantly clearer window into the nature and extent of cellphone searches.
Enact Robust Data Deletion and Sealing Requirements
State and local lawmakers should require law enforcement to delete any extracted cellphone data that is not related to the objective of the warrant within thirty days from the date the information is obtained. In addition, for cases that result in a conviction, data that was deemed relevant should be sealed at the conclusion of the case. For other cases, where charges are dismissed or do not result in conviction, all data should be deleted, relevant or not. Data deemed relevant in one case should never be used for general intelligence purposes or used in unrelated cases.
As we explained in Section 5, in the absence of clear law or policy, law enforcement could use personal information like contact lists, photos, and location data to fuel police surveillance systems. This is true not only of the data of the person whose phone was searched, but also that of anyone they have been in contact with using their phone. Cellphone searches are unlike traditional seizures because law enforcement extracts all of the data on the device and subsequently searches for case-relevant information. Maintaining information outside the scope of the warrant is akin to law enforcement maintaining the ability to indefinitely and limitlessly search a home.
Policies requiring this kind of data deletion or sealing already exist in New Mexico, Utah, and California. Additionally, New York requires all arrest records for any person not convicted of a crime to be sealed.
There is clear potential for abuse of this kind of policy if law enforcement unilaterally determines the relevancy of data to the warrant. Such abuse can partially be mitigated by requiring clear defense access to the extracted data so they can challenge law enforcement’s inclusion or exclusion of information. Audit logs would also help.
Clear retention requirements could not only help hold law enforcement accountable to the scope of the warrant, but could also significantly limit the data that law enforcement could include in internal systems like intelligence databases, “gang databases,” and predictive policing tools.
Require Clear Public Logging of Law Enforcement Use
State and local policymakers should require public reporting and logging for how law enforcement use mobile device forensic tools. These records should be released at least monthly, as this would allow more immediate access to information by advocates, policymakers, and the public seeking to understand the capabilities of their police agency. Agencies should additionally release annual reports on overall department usage.
These records should include aggregate information on how law enforcement is using MDFTs, including:
How many phones were searched in a given time period.
Whether those searches were by consent (though consent searches should be banned), or through a warrant.
Warrant numbers associated with searches, when applicable.
The type(s) of offenses being investigated.
How often the tools led to successful data extractions.
Explanations for any failed extractions.
Which tools were used for extraction and analysis, and their version numbers.
Understanding how, when, and under what legal authority law enforcement use these powerful technologies can increase transparency and accountability. Beyond mere transparency, these kinds of records are important as they can help advocates, researchers, policymakers, and the public effectively pursue policies that reduce the power and scope of law enforcement. More broadly, these kinds of records can help challenge law enforcement’s narrative surrounding how, when, and why these tools are used.
While this kind of public reporting can be helpful, it will not inherently lead to a responsible or decreased use of MDFTs by law enforcement. Take wiretapping as an example. Federal law requires an annual reporting of the number of “applications for orders authorizing or approving the interception of wire, oral, or electronic communications.” But there is evidence of widespread underreporting of wiretaps. Transparency reports published by wireless service providers like AT&T, Sprint, T-Mobile, and Verizon “state that they implemented three times as many wiretaps as the total number reported by the Administrative Office of the Courts.” This casts doubt on whether public reporting of MDFT usage will accurately represent their usage by law enforcement. Worse, law enforcement could manipulate these records in order to justify increased funding. However, given that MDFT reporting should include warrant numbers and more detailed information than Title III reporting requires, there is less opportunity for the inaccuracies rampant in aggregate reporting.
Ultimately, this information will still be useful even if incomplete. Policymakers and advocates should remain cautious in using the information agencies report, and cross-reference with other sources of information, like warrants, public records, and reports from individuals and public defenders.
Conclusion
Our research shows that every American is at risk of having their phone forensically searched by law enforcement. Significantly more local law enforcement agencies have access to this technology than previously understood. These agencies use the tools far more than previously documented, and use them in a broad array of cases. They do so with few policies or legal constraints in place. Given how routine these searches are today, and given racist policing practices, it’s more than likely that these technologies disparately affect and are used against communities of color. Put together, this report documents a dangerous expansion in law enforcement’s investigatory power.
Put together, this report documents a dangerous expansion in law enforcement’s investigatory power.
For too long, public debate and discussion regarding these tools has been abstracted to the rarest and most sensational cases in which law enforcement cannot gain access to cellphone data. We hope that this report will help recenter the conversation regarding law enforcement’s use of mobile device forensic tools to the on-the-ground reality of cellphone searches today in the United States.
Acknowledgements
This work would not be possible without the tireless work of our colleagues and partners. We are grateful to them, and we take responsibility for any errors that remain here. Special thanks to Jerome Greco and The Legal Aid Society for allowing us to visit their Digital Forensics Unit, and for providing us with assistance since the beginning of this project. Also special thanks to Cameron Cantrell and Sarika Ram for their research as Summer Fellows at Upturn, and to Ming Hsu for his work on the maps in this report.
For their helpful input and feedback on this report, we’d like to thank several individuals: Khalil A. Cumberbatch, Senior Fellow, The Council on Criminal Justice; Jennifer Granick, Surveillance and Cybersecurity Counsel, ACLU Speech, Privacy, and Technology Project; Jerome Greco, Digital Forensics Supervising Attorney, Digital Forensics Unit/Criminal Defense Practice, The Legal Aid Society; Jennifer Lynch, Surveillance Litigation Director, Electronic Frontier Foundation; Jumana Musa, Fourth Amendment Center Director, National Association of Criminal Defense Lawyers; David Robinson, Visiting Scientist, AI Policy and Practice Initiative, Cornell's College of Computing and Information Science; Hannah Jane Sassaman, Policy Director, Movement Alliance Project; and Vincent Southerland, Executive Director Center on Race, Inequality, and the Law, New York University School of Law. We’d also like to thank Clare Garvie, Senior Associate at the Center on Privacy & Technology at Georgetown Law for early help in structuring our public records request project. All affiliations are for identification purposes only.
For pro bono representation of Upturn in our litigation under New York’s Freedom of Information Law to compel the NYPD to produce documents related to its use of mobile device forensic tools, we’d also like to thank Albert Fox Cahn, the Executive Director of the Surveillance Technology Oversight Project and Shearman & Sterling, LLP.
Thanks to Objectively for assisting with the design of our report and to Spitfire Strategies for communications and press outreach.
Upturn is supported by the Ford Foundation, the Open Society Foundations, the John D. and Catherine T. MacArthur Foundation, Luminate, the Patrick J. McGovern Foundation, and Democracy Fund.
Appendix A: Methodology
In order to determine how many law enforcement agencies have purchased mobile device forensic tools, we sent more than 110 public records requests to a wide range of law enforcement agencies.
We began our public records survey in February 2019. We sent public records requests to a variety of law enforcement agencies: police departments, sheriff offices, district attorneys’ and prosecuting offices, state law enforcement, and forensics labs across the country. We also sent records requests to Departments of Finances and Departments of Procurement, many of which keep records of purchases. We sent records requests to the country's 50 largest local police departments, as well as many of the largest state law enforcement agencies. We also sent requests to smaller law enforcement agencies where previous public reporting indicated the purchase of MDFTs.
Many departments provided us some records in response to our requests — some provided full responses, some provided limited responses. As we expected, some departments denied our requests. For example, both the Baltimore and Cincinnati Police Departments denied our requests based on investigatory methods and technique exemption to public disclosure. Others quoted exorbitant fees to fulfill our records request, which we’ve declined to pay. For example, the Fairfax County (VA) Police Department quoted us $10,349, the Missouri State Highway Patrol quoted us $1,324, and the Jacksonville Sheriff’s Office quoted us more than $700,000 to fulfill our requests. Other agencies simply have not responded in a determinative way.
Beyond public records requests to individual agencies, we supplemented our research in four other ways.
First, we explored existing, publicly available reporting or information, through services like MuckRock or other media reporting.
Second, we explored various open databases from city, county, and state governments, which document spending and vendor payments. Such databases often provide a transparent view into government purchasing as a whole, and contain specific purchasing information on MDFTs. In many instances, these databases helped us determine if a police department had purchased MDFTs, even if the department denied our records request. For example, although the Cincinnati Police Department denied our records request, a publicly available dataset indicates the police department paid more than $100,000 to vendors like Cellebrite, Grayshift, and MSAB. Similarly, although the Detroit Police Department quoted us over $1,000 to fulfill our request, the City of Detroit’s Open Data Portal reveals that the Detroit Police Department paid at least $30,000 to Cellebrite.
Third, we searched databases that document federal grantmaking to local law enforcement agencies. Some data on federal grants helped us determine that a law enforcement agency purchasedMDFTs even if the agency denied our records request. For example, although the Bronx District Attorney’s Office denied our request, the office is, among other things, funded through the Coverdell Forensics Science Improvement Grant to “to acquire the Cellebrite Advanced Universal Forensic Extraction Device software solution.”
Finally, we used GovSpend, which is a database of government contracts and purchase orders. GovSpend aggregates purchase order data from local, state, and federal government agencies, to provide inter-agency transparency on costs. The database is also open to certain non-governmental parties, like news media organizations. We used GovSpend to better understand the scale of MDFT purchases across the country.
In all, we received more than 12,000 pages of documents in response to our records requests.
Appendix B: Public Records Request Template
[Date]
[Agency Address]
Re: [State Records Request Law] Request
To Whom it May Concern:
This is a request under the [State Records Request Law and citation], on behalf of Upturn, a 501(c)(3) nonprofit organization based in Washington D.C. Our mission is to promote equity and justice in the design, governance, and use of digital technology. This request seeks records relating to the [Agency’s] use of mobile device forensic technologies, as well as the Department’s policies and procedures governing such use.
Background
Due to the ubiquity of mobile devices, law enforcement sees the data stored on mobile devices, like cellphones, as key sources of evidence for investigations. However, mobile devices can contain large amounts of people’s sensitive and private information, much of which may be irrelevant to a given investigation. As the Supreme Court recognized five years ago in Riley v. California, “[o]ne of the most notable distinguishing features of modern cellphones is their immense storage capacity.” As such, forensic searches of mobile devices are often highly invasive, and we believe that such searches by law enforcement are increasingly common.
Mobile device forensic tools (MDFTs) are used by law enforcement to extract data from mobile devices.Generally speaking, two different kinds of extraction, logical and physical, give different scopes of data access — the latter including deleted data, system-level metadata, and other data normally inaccessible from the device’s user interface. In some cases, if the data on the mobile device is encrypted, some MDFTs can help law enforcement circumvent a device's security features in order to access otherwise inaccessible data. These capabilities have been the subject of broad public debate, for example, in the aftermath of the high-profile San Bernardino shooting in 2015. Whether or not devices are encrypted, law enforcement’s use of MDFTs is an issue of significant public interest.
Currently, there is a considerable lack of public information available regarding how local law enforcement agencies use MDFTs, and the policies and procedures that govern such use. The public is entitled to understand the Department’s activities and capabilities with respect to MDFTs, and this request seeks to further the public’s understanding.
Public Records Request
Upturn seeks records regarding the Department’s use of mobile device forensic tools (MDFTs). This includes any software, hardware, process, or service that is capable of any of the following:
extracting any data from a mobile device,
recovering deleted files from a mobile device, or
bypassing mobile device passwords, locks, or other security features.
Examples of MDFTs include, but are not limited to, products or services offered by vendors such as Cellebrite, Grayshift, Oxygen Forensics, BlackBag Technologies, Magnet Forensics, MSAB, AccessData, Paraben, Katana Forensics, BK Forensics, and Guidance Software/OpenText.
Upturn specifically requests the following records under the [applicable state law]:
Purchase Records and Agreements: Any and all records reflecting an agreement for purchase, acquisition, or license of MDFTs, or permission to use, test, or evaluate MDFTs since 2015.
Records of Use: Any and all records describing the Department’s use of MDFTs since 2015.
a. In particular, we seek records reflecting the department’s aggregate use of MDFTs. For example, monthly reports that reflect total number of MDFT cases for each month, broken down by type of crime, and number and type of phones, and number and type of other devices.
i. Please specify any instances where the department used Cellebrite Advanced Services, or otherwise transferred possession of a device or its contents to a vendor for off-site processing, including Regional Computer Forensics Laboratories.
ii. Please include any instances of forensic examination of a device (e.g. using JTAG or chip-off processes) that may not involve a vendor’s product.
Policies Governing Use: Any and all records regarding policies and guidelines governing the use of MDFTs, including but not limited to: training materials regarding their operation, restrictions on when they may be used, limitations on retention and use of collected data, security measures taken to protect stored and in-transit data, guidance on when a warrant or other legal process must be obtained, and guidance on when the existence and use of MDFTs may be revealed to the public, criminal defendants, or judges.
Information About the Request
Upturn appreciates [Agency's] attention to this request. According to [applicable state law], your agency must comply with a request [within X business days / timeframe]. Further, under [applicable state law] we request a fee waiver. As Upturn is a non-profit organization, and disclosure of requested records will promote public awareness and knowledge of governmental action, we are requesting that fees associated with this request be waived. If you determine that a fee waiver is not appropriate in this instance, and if the estimated cost associated with fulfilling this request exceeds $25, please contact me before proceeding to fulfill our request.
Please furnish all applicable records in electronic format to records@upturn.org. For records available only in a physical format, please send such records to:
Upturn
1015 15th St. N.W. Suite 600
Washington, D.C., 20005
Should you have any questions concerning this request, please contact Logan Koepke by telephone at (214) 801-4499 or via e-mail at logan@upturn.org.
Sincerely,
Appendix C: Total Amounts Spent on MDFTs
Based on agency responses to our public records requests, the following table provides total amounts each agency has spent on MDFTs since 2015. These figures represent lower bounds on the amounts actually spent, since records responses may be incomplete.
| Law Enforcement Agency | Amount Spent (at least) | Vendors |
|---|---|---|
| Anoka County Sheriff | $34,205 | AccessData, BlackBag Technologies, Cellebrite, CRU, Guidance Software, Katana Forensics, Magnet Forensics, Micron Consumer Products Group, MSAB, Paraben Corporation |
| Arizona Department of Public Safety | $110,605 | Grayshift, Cellebrite, BlackBag Technologies, Magnet Forensics, Tritech Forensics |
| Atlanta Police Department | Unknown | Unknown |
| Austin Police Department | $92,719 | AccessData, BlackBag Technologies, Cellebrite, Grayshift, Guidance Software, Magnet Forensics |
| Baltimore County Police Department | Unknown | Unknown |
| Bend Police Department | $62,761 | Cellebrite |
| Bernalillo District Attorney | $35,354 | Cellebrite |
| Broward County Sheriff | $563,091 | Cellebrite, Grayshift, Oxygen Forensics, Magnet Forensics, MSAB, BlackBag Technologies, AccessData, Katana Forensics, Guidance Software |
| California DOJ | $225,449 | Cellebrite |
| California Highway Patrol | $25,289 | BlackBag Technologies, Cellebrite, MSAB |
| Charlotte-Mecklenburg Police Department | $181,557 | BlackBag Technologies, Cellebrite, Grayshift, MSAB |
| Chicago Police Department | $31,830 | Cellebrite |
| City of Miami Police Department | $66,558 | Cellebrite |
| Collin County Sheriff | $90,724 | Cellebrite, Magnet Forensics |
| Colorado State Patrol | $56,345 | Cellebrite, Federal Law Enforcement Training CT |
| Columbus Police Department | $114,656 | AccessData, Grayshift, Magnet Forensics, Oxygen Forensics, Cellebrite |
| Cook County District Attorney | $17,495 | Cellebrite |
| Cook County Sheriff’s Office | $37,342 | Cellebrite |
| Dallas County District Attorney | $4,902 | AccessData, BlackBag Technologies, Cellebrite, Katana Forensics |
| Dallas Police Department | $482,542 | Cellebrite, GTS Technology Solutions, Cellebrite1 |
| DC Department of Forensic Sciences | $57,414 | Cellebrite, MSAB |
| DC Metropolitan Police Department | $21,693 | Cellebrite |
| DeKalb Police Department | $4,865 | AccessData |
| Denver Police Department | $51,170 | Cellebrite, Cellebrite |
| El Paso Police Department | Unknown | Unknown |
| Fairfax County Police Department | Unknown | Unknown |
| Fort Worth Police Department | $120,921 | AccessData, BlackBag Technologies, Cellebrite, Grayshift, MSAB, Oxygen Forensics, Magnet Forensics |
| Gwinnett County District Attorney | $66,388 | H-11 Digital Forensics, Cellebrite, Oxygen Forensics, Magnet Forensics, Susteen, Cleverbridge, Passware |
| Harris County Sheriff | $176,854 | BlackBag Technologies, Cellebrite, Katana Forensics, Magnet Forensics, MSAB |
| Hennepin County Sheriff | $59,661 | Cellebrite, Grayshift |
| Honolulu Police Department | $60,212 | Cellebrite |
| Houston Police Department | $210,255 | AccessData, Cellebrite, Magnet Forensics, MSAB |
| Illinois State Police | $157,147 | Cellebrite, Grayshift, Guidance Software, Magnet Forensics |
| Indiana State Police | $513,517 | BlackBag Technologies, Cellebrite, Magnet Forensics, Grayshift, Katana Forensics, MSAB, OpenText, Oxygen Forensics |
| Indianapolis Metropolitan Police Department | $153,341 | BlackBag Technologies, Cellebrite, Grayshift, Guidance Software, Katana Forensics, Magnet Forensics, MSAB |
| Iowa Department of Public Safety | $133,324 | Cellebrite |
| Jacksonville County Sheriff | $22,728 | Grayshift, Cellebrite |
| Jefferson Parish Sheriff’s Office | Unknown | Unknown |
| Kansas City Police Department | $81,688 | Cellebrite |
| Las Vegas Metropolitan Police Department | $646,229 | AccessData, BlackBag Technologies, Cellebrite, Guidance Software, Katana Forensics, Magnet Forensics, MSAB, EnCase Forensics |
| Los Angeles District Attorney | $55,795 | Cellebrite, Grayshift |
| Los Angeles Police Department | $358,426 | BlackBag Technologies, MSAB, Cellebrite, Guidance Software |
| Louisville Metro Police Department | $65,692 | Cellebrite |
| Manhattan District Attorney | $638,676 | Cellebrite |
| Massachusetts State Police | Unknown | Unknown |
| Miami Dade Police Department | $337,072 | Cellebrite |
| Milwaukee Police Department | $7,400 | Cellebrite |
| Modesto Police Department | $147,117 | BlackBag Technologies, Grayshift, Cellebrite, AccessData |
| Nassau Police Department | $64,274 | Cellebrite, MSAB, Oxygen Forensics |
| New York County District Attorney | $495,315 | Cellebrite, BlackBag Technologies, Final Data, Forensic Computers Inc, Grayshift, Magnet Forensics, MSAB, EnCase Forensics, AccessData, Teel |
| New York Police Department | $30,000 | Grayshift |
| North Carolina Department Public Safety | $122,621 | AccessData, Cellebrite, Guidance Software, Katana Forensics, Magnet Forensics, MSAB, OpenText |
| Ohio State Highway Patrol | $75,088 | BlackBag Technologies, Cellebrite, Grayshift, Magnet Forensics |
| Oklahoma City Police Department | $33,890 | Cellebrite, Grayshift, Magnet Forensics, AccessData |
| Orange County District Attorney | $24,187 | Cellebrite, Susteen |
| Pennsylvania State Police | $540,625 | Cellebrite, Magnet Forensics, MSAB, Grayshift, Oxygen Forensics |
| Pennsylvania State Police | $623,929 | Cellebrite, Magnet Forensics, MSAB, Grayshift, Oxygen Forensics |
| Philadelphia District Attorney | $64,506 | AccessData, Cellebrite, Katana Forensics, Magnet Forensics |
| Phoenix Police Department | $117,460 | Cellebrite |
| Portland Police Bureau | $261,119 | AccessData, Cellebrite, Grayshift, Magnet Forensics, MSAB, Oxygen Forensics |
| Prince George’s Police Department | $67,300 | Cellebrite |
| Riverside County Sheriff | $180,535 | Cellebrite |
| Sacramento Police Department | $94,051 | Cellebrite, Grayshift, EnCase Forensics |
| San Bernardino Sheriff | $270,380 | BlackBag Technologies, Cellebrite, Guidance Software, Magnet Forensics, MSAB |
| San Diego District Attorney | $164,499 | Cellebrite, Grayshift, Magnet Forensics, MSAB |
| San Diego Police Department | $232,999 | Cellebrite, Grayshift, Magnet Forensics, MSAB, OMC2 LLC/Bantam Tools, Teel |
| San Francisco Police Department | $40,935 | Cellebrite |
| San Jose Police Department | $296,363 | BlackBag Technologies, Cellebrite, Grayshift, Guidance Software, Katana Forensics, Magnet Forensics, MSAB |
| Santa Clara District Attorney | $233,203 | Grayshift, Cellebrite, MSAB, AccessData, Guidance Software |
| Seattle Police Department | $240,837 | Cellebrite, MSAB, Magnet Forensics, Grayshift |
| Spokane Police Department | $255,369 | Cellebrite |
| St. Joseph County Prosecutor | $14,626 | AccessData, Cellebrite, Magnet Forensics |
| St. Louis Police Department | $26,652 | AccessData, BlackBag Technologies, Cellebrite, MSAB, Oxygen Forensics |
| Suffolk County District Attorney | $31,195 | Cellebrite |
| Suffolk County Police Department | $34,671 | BlackBag Technologies, Cellebrite, Grayshift, Guidance Software, Magnet Forensics, OpenText |
| Tampa Police Department | Unknown | Unknown |
| Tarrant County District Attorney | $9,986 | AccessData, Magnet Forensics |
| Texas Department of Public Safety | $188,782 | BlackBag Technologies, Grayshift, Cellebrite, Magnet Forensics, MSAB, EnCase Forensics, Oxygen Forensics |
| Travis County District Attorney | $171,980 | Cellebrite, Grayshift, MSAB, Guidance Software, OpenText, EnCase Forensics, Teel, Magnet Forensics, BlackBag Technologies |
| Travis County Sheriff’s Office | Unknown | Unknown |
| Tucson Police Department | $126,958 | AccessData, Cellebrite, Grayshift, Magnet Forensics, MSAB, Sanderson Forensics |
| Tulsa Police Department | Unknown | Cellebrite, Susteen |
| Washington State Patrol | $52,343 | Cellebrite, Magnet Forensics |
| West Allis Police Department | $10,397 | Cellebrite |
Related Work
Upturn, Inc. v. New York City Police Department
We are suing the NYPD for records concerning the department’s use of mobile device forensic technology. Upturn is represented on a pro-bono basis by Shearman & Sterling, LLP and the Surveillance Technology Oversight Project (S.T.O.P.).